Customer Spotlight: Zeta Global Streamlines Snowflake Data Access Management and Reduces Operational Complexity of Managing Multiple Accounts
Stay in the Know
Subscribe to Our Blog
Thanks to co-author Karthik Reddy-Sathya, Engineering Manager with Zeta Global, for his valuable contributions to this blog post.
Zeta is a leading data-driven, cloud-based marketing technology company that empowers enterprises to acquire, grow and retain customers. The Zeta Marketing Platform (ZMP) is the largest omnichannel marketing platform with identity data at its core. The ZMP analyzes billions of structured and unstructured data points to predict consumer intent by leveraging sophisticated artificial intelligence to personalize experiences at scale.
Zeta Global Growth with Snowflake
The company maintains high volume and high frequency proprietary opt-in datasets that are among the largest in the world, spanning numerous Snowflake accounts across two continents, to generate unique insights on consumer intent. Zeta leverages Snowflake's flexible compute and storage scalability to support its customers across multiple regions and still be compliant with data residency and data governance regulations.
Operational Efficiency Challenges
The growth in data sets and number of Snowflake accounts has led to an explosion of data consumers, roles, access control rules, and permissions. This creates a challenge for the data platform team responsible for securely granting access to the various internal staff and external customers. This small team has a big responsibility: securing sensitive personal identifiable information (PIl) and granting access to all of Zeta Global’s own data scientists, engineers, and business analysts along with the clients' stakeholders. This team was receiving a steady stream of troubleshooting tickets for new data access or adjusting existing access. In addition to this, they are also responsible for providing data access reports to the security team on an ad-hoc basis.
With multiple accounts, and customer specific databases, the team was spending a considerable amount of time reverse engineering the answers to the following questions:
- What is the appropriate role to grant in the role hierarchy for a given request?
- Does the user already have access to data via another role?
- Should we create a new role to grant access to new data sets?
- Which users have access to current data set?
In addition to day-to-day access request grants, the spontaneous requests for compliance and audit requests were taking 24 hours or more as the team had to perform SQL queries and correlated information to satisfy the requests.
Unused Data Challenges
Zeta Global uses six Snowflake accounts for development, testing, demonstrations, and production. This set-up brought in another operational challenge: managing unused copies of data shared across all of these accounts. This data includes sample data sets created for demos and data copied from one environment to another for test and validation purposes. These copies were originally created for specific development, test or demo tasks, but were not removed when those tasks were completed. This unused data was increasing their cloud storage costs, as well as requiring much manual effort to find and remove such data in order to avoid compliance violations.
How TrustLogix is Helping Zeta Global
Zeta Global required a centralized cloud-native platform to simplify data security and governance across its multi-account cloud environment. TrustLogix provides a proxy-less, agentless architecture that ensures data stays in customers’ Snowflake accounts without any barrier between data consumer and data platform.
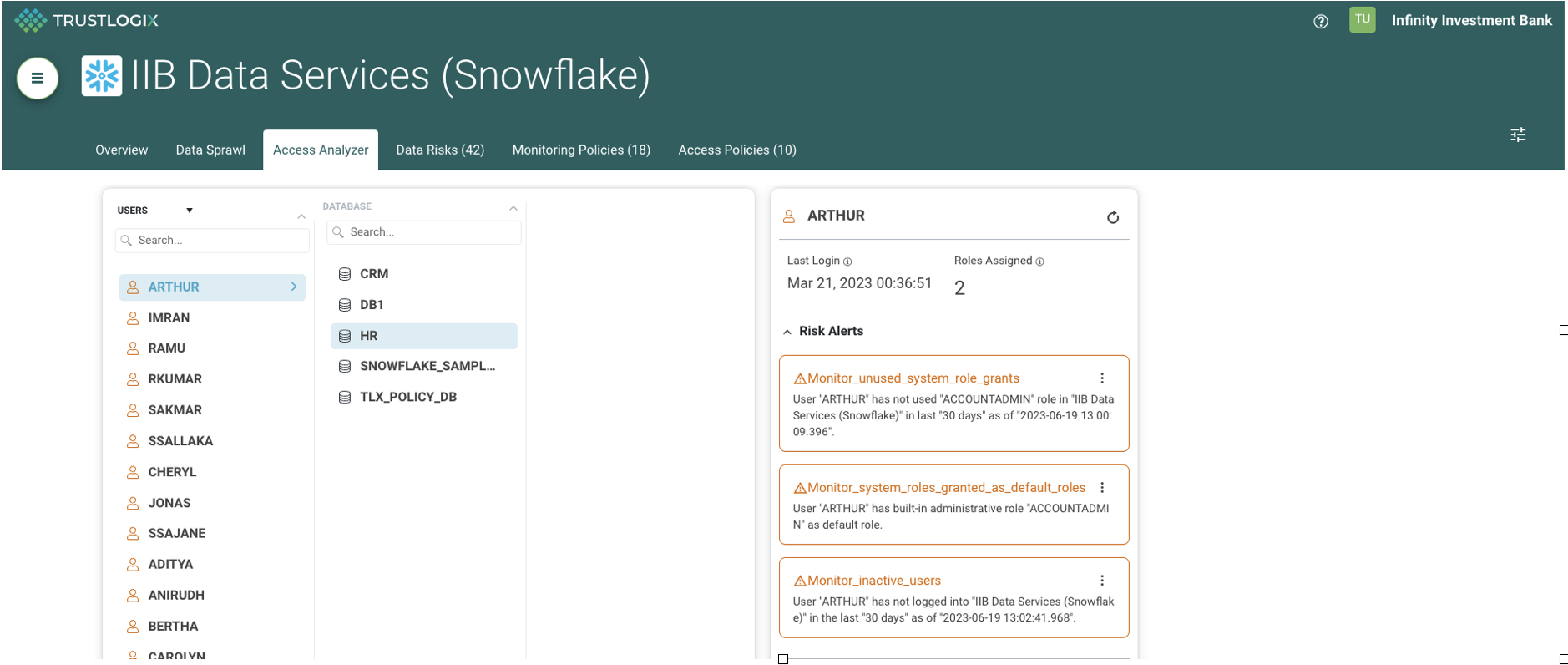
TrustLogix’s Access Analyzer tool provides a simplified business user friendly GUI to understand the role hierarchy, user-to-role access grants, and data-to-role grants. Furthermore, with a few clicks one can assign or revoke access roles to users and other access roles. This streamlines the process of addressing new access requests. In addition, TrustLogix also provides meaningful insights to right size any existing roles to maintain Least Privilege access model.
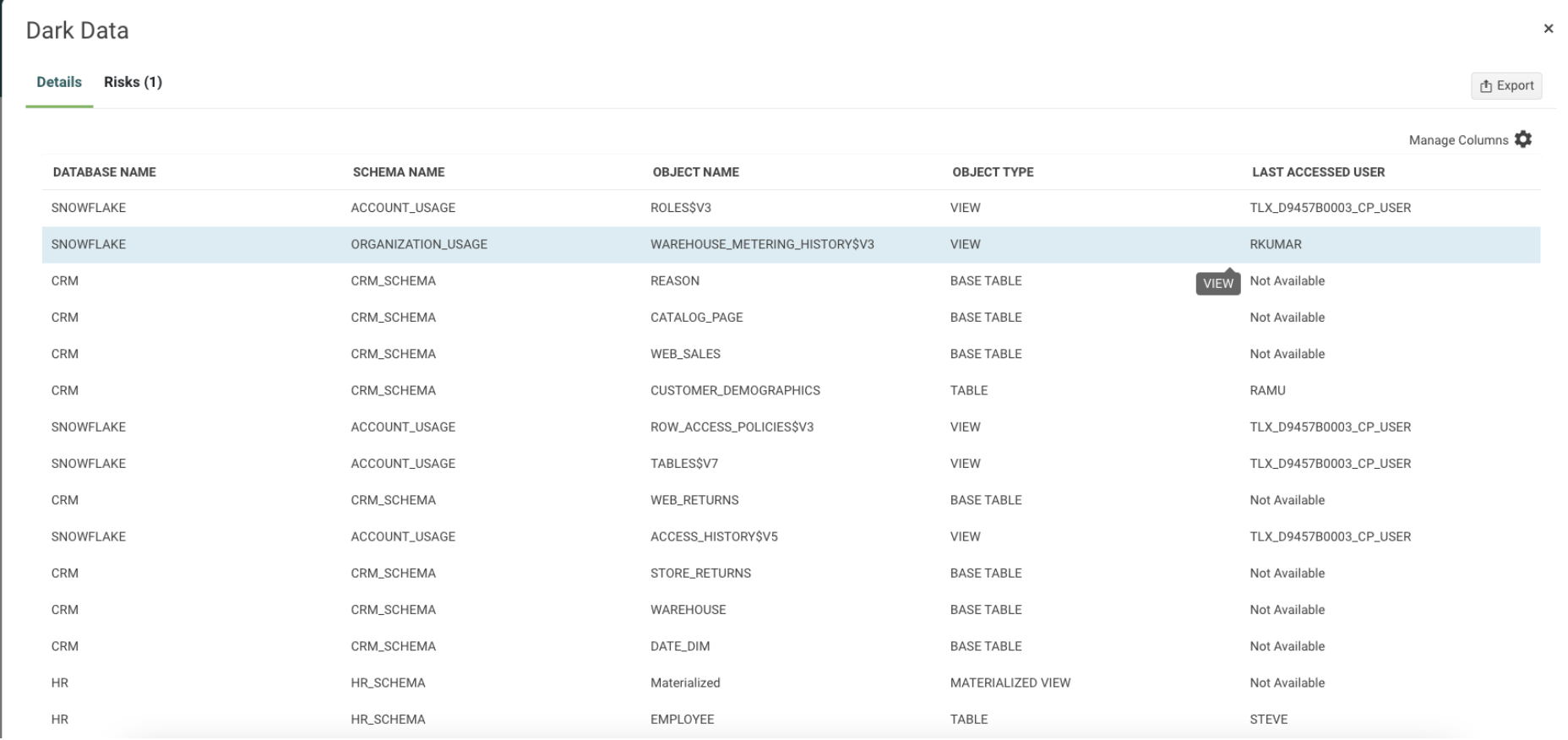
Dark Data Report
TrustLogix provides a report that summarizes which data sets were not used in the last 60 days, who created the data sets, and who accessed it last. This report is leveraged to follow up with respective data teams to either retire the data or archive it for a future purpose. This ensures that Zeta Global is constantly reducing the attack surface by keeping only fresh and relevant data in the Snowflake data warehouse.
Additional Findings with TrustLogix DSPM
Overly Granted Users
TrustLogix provides Zeta Global with the ability to discover and observe the data policies in place. One of the most critical findings it uncovered was that instead of the usual 3-4 admin users, the company had 35 users who had been issued admin privileges. This overly granted access can lead to violation of its Separation of Duties (SoD) controls. Another 100+ inactive user accounts were found to have highly privileged access and hadn't been used in many months (ghost accounts). As with the overly granted privilege, this excessive granting of access can create the potential for insider misuse and compliance risk.
In Conclusion
As a leading global marketing technology firm Zeta Global needs to stay at the forefront of data privacy and security. They are vital to Zeta’s customers and prospects, who entrust us with their consumer PII and intent data. With TrustLogix, Zeta Global can confidently scale its data security operations as data volumes and data consumers increase, can easily demonstrate compliance with current regulations, and will enable complying with more data residency and privacy laws that may be enacted in the future.
