Simplify Your Data Controls
Cloud Data Access Governance Delivers Central Management of Privacy, Security, & Availability
AUTOMATED CLOUD DATA SECURITY THAT IS FAST, SAFE, EASY, AND AUDITABLE
TrustLogix makes Cloud Data Access Governance secure, fast, safe, easy, and auditable
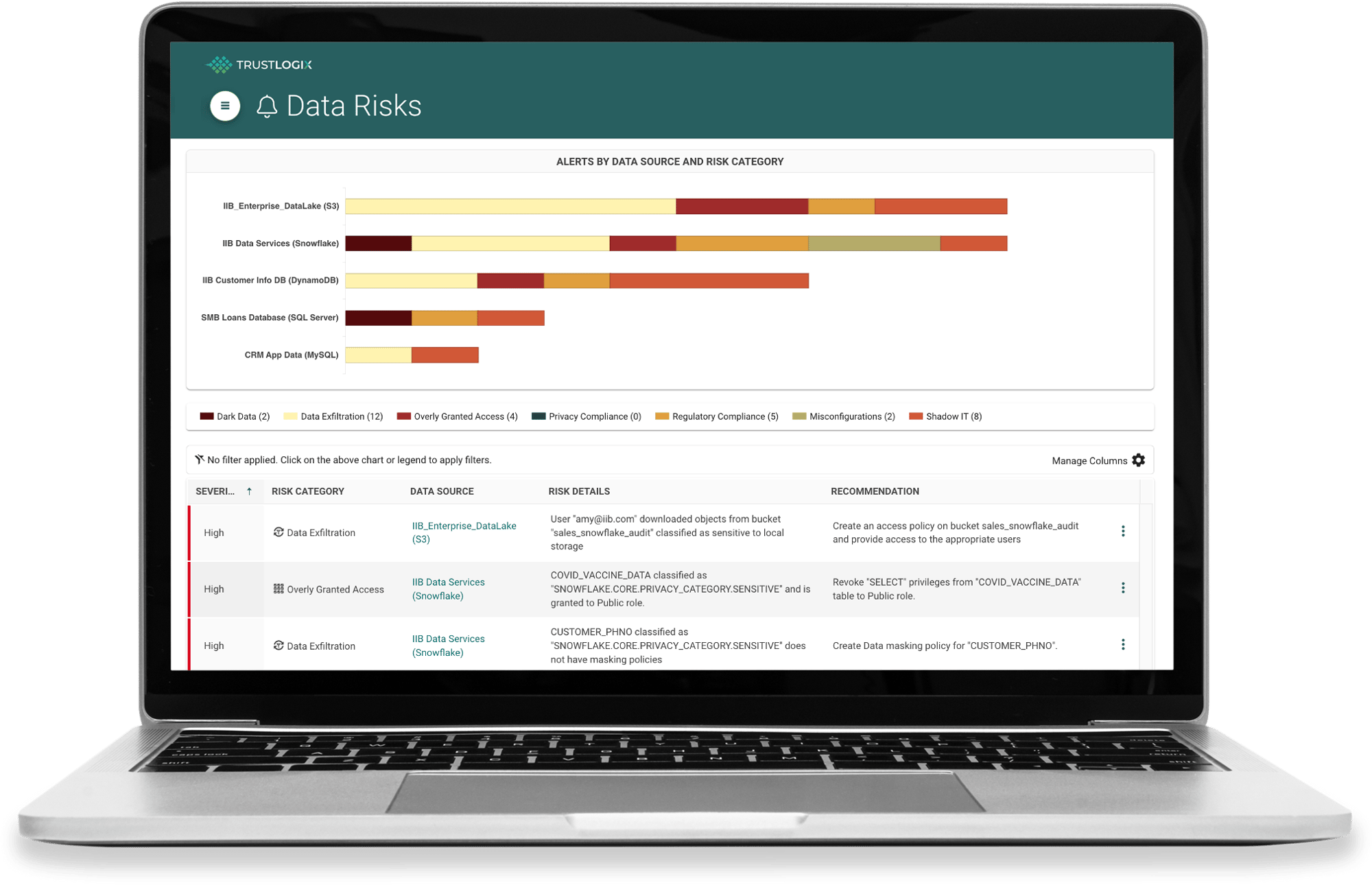
Instant Visibility into Data Risks Across All Your Data Stores
Your team has total visibility into data risk, broken out by data source and type of risk.
.png?width=1908&height=850&name=Alerts%20(Top%20Half).png)
Prevent Small Problems from Becoming Big Nightmares with Categorized Alerting
Rich alerting capabilities enable your team to mitigate data risk exposure across Dark Data, Data Exfiltration, Overly Granted Access, Privacy Compliance, Regulatory Compliance, Misconfiguration, and Shadow IT.
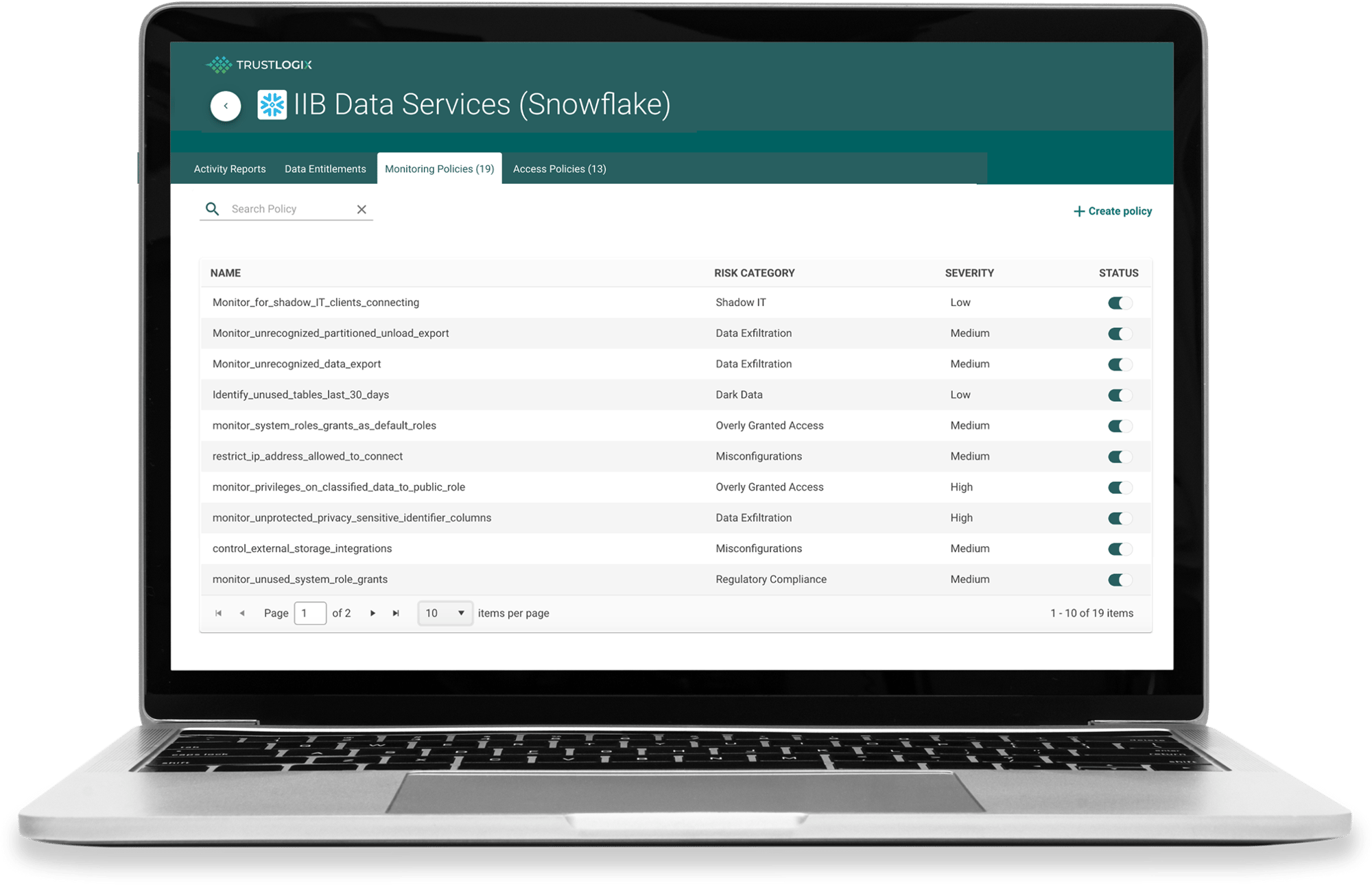
Tailored Policy Recommendations Based on AI-Modeled Best Practices
Your team gets customized recommendations for tuning data access controls based on a combination of industry best practices and observed data access activity in your environment.
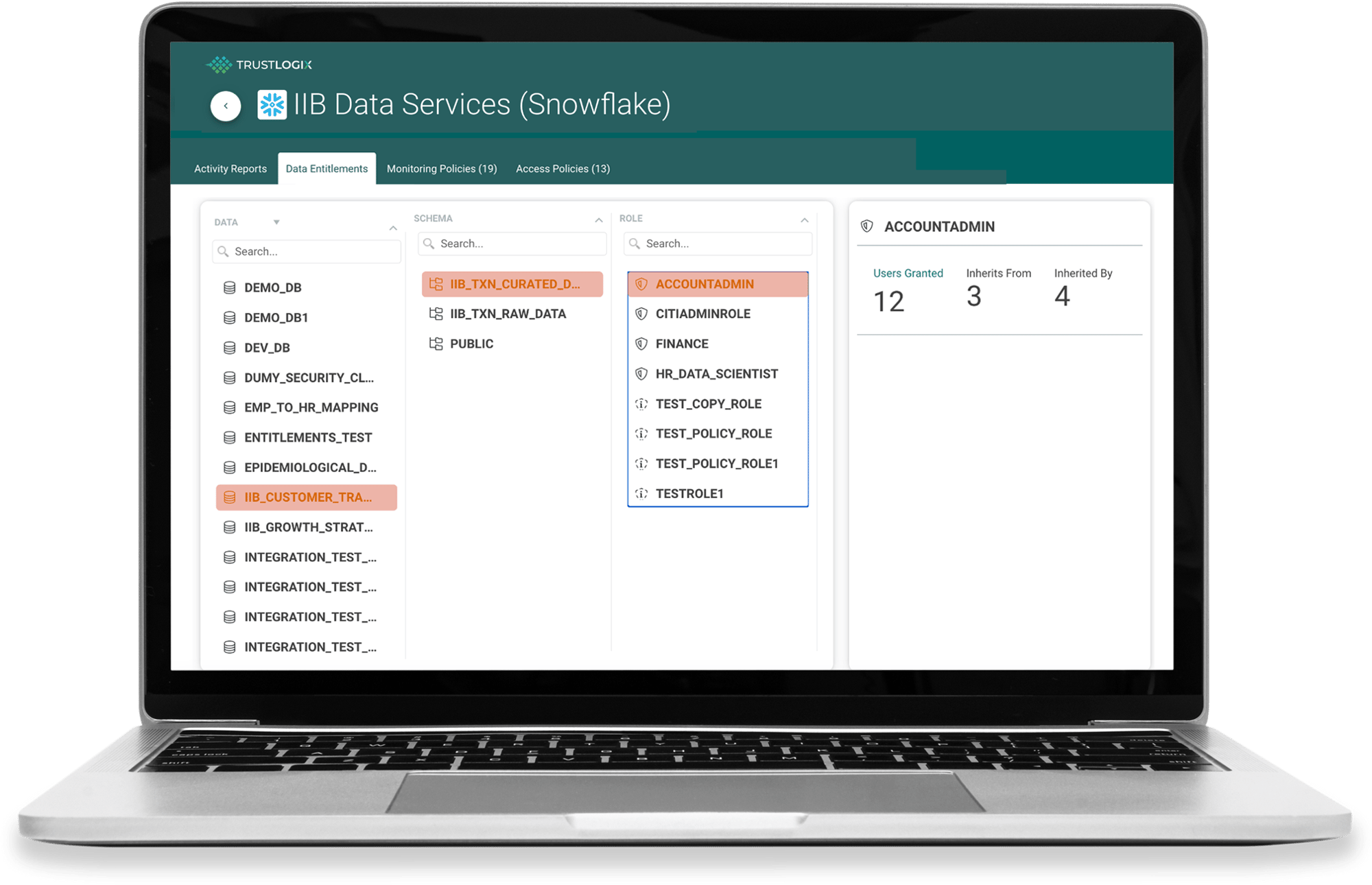
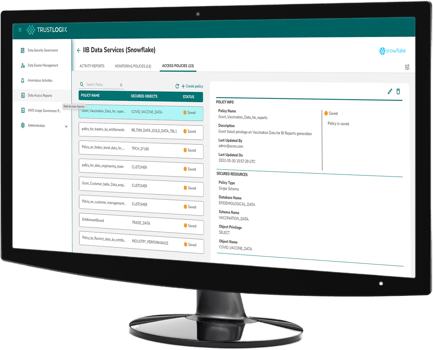
Fine-Grained Data Security, with Advanced Policy Orchestration and Enforcement
No-code policy administration tools give your team access policies, run-time entitlements, and fine-grained data access controls that protect your organization. TrustLogix delivers precise data access control with different types of policies, including column masking, row and column filtering, and tag-based policies, by integrating with your data classification engine.
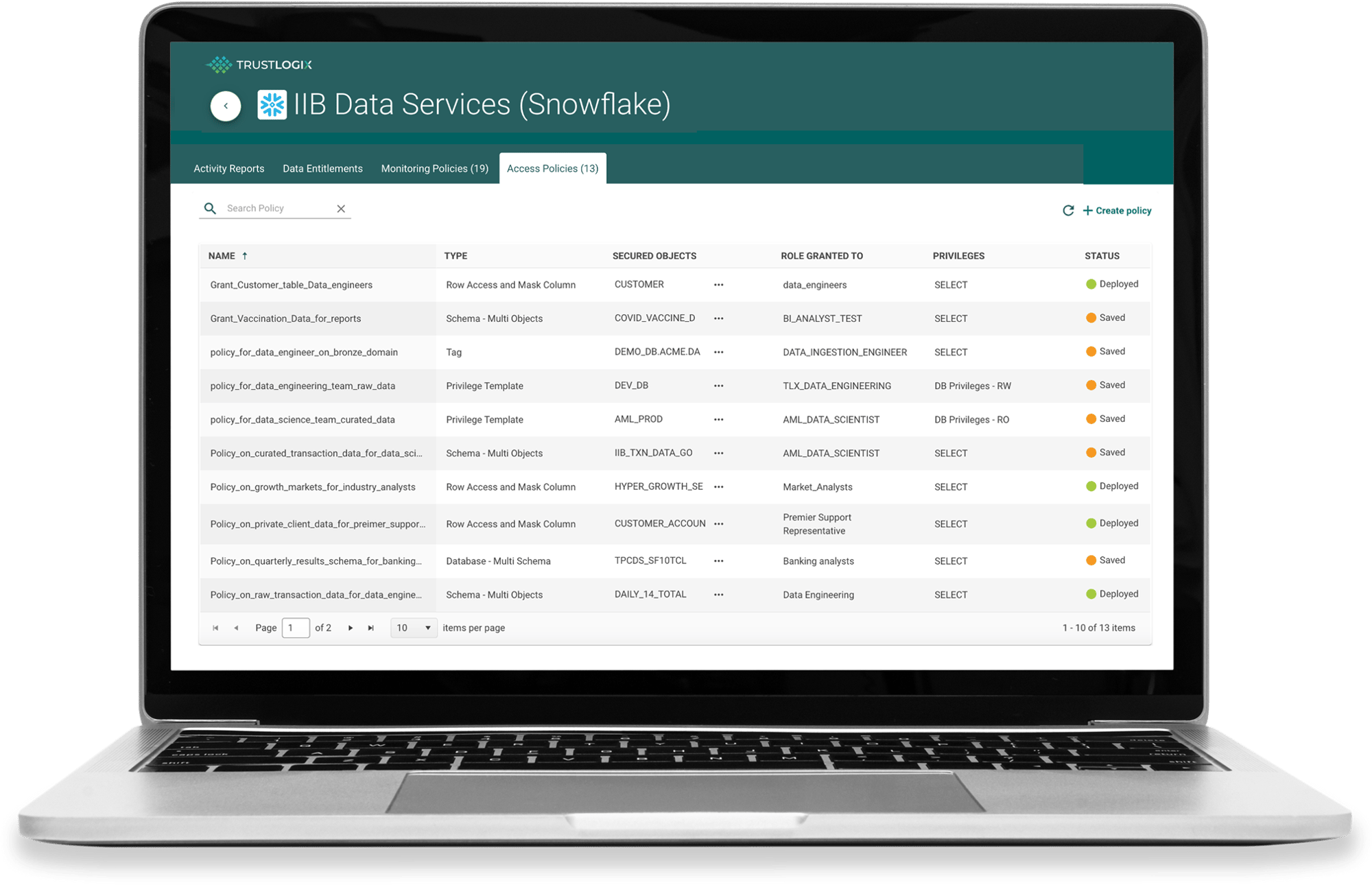
Instant No-Code Policy Administration, Saving Your Team Time and Reducing Errors with SQL
Auto-generate and instantly deploy SQL constructs for each data platform across multiple accounts and data stores using English-based rules.
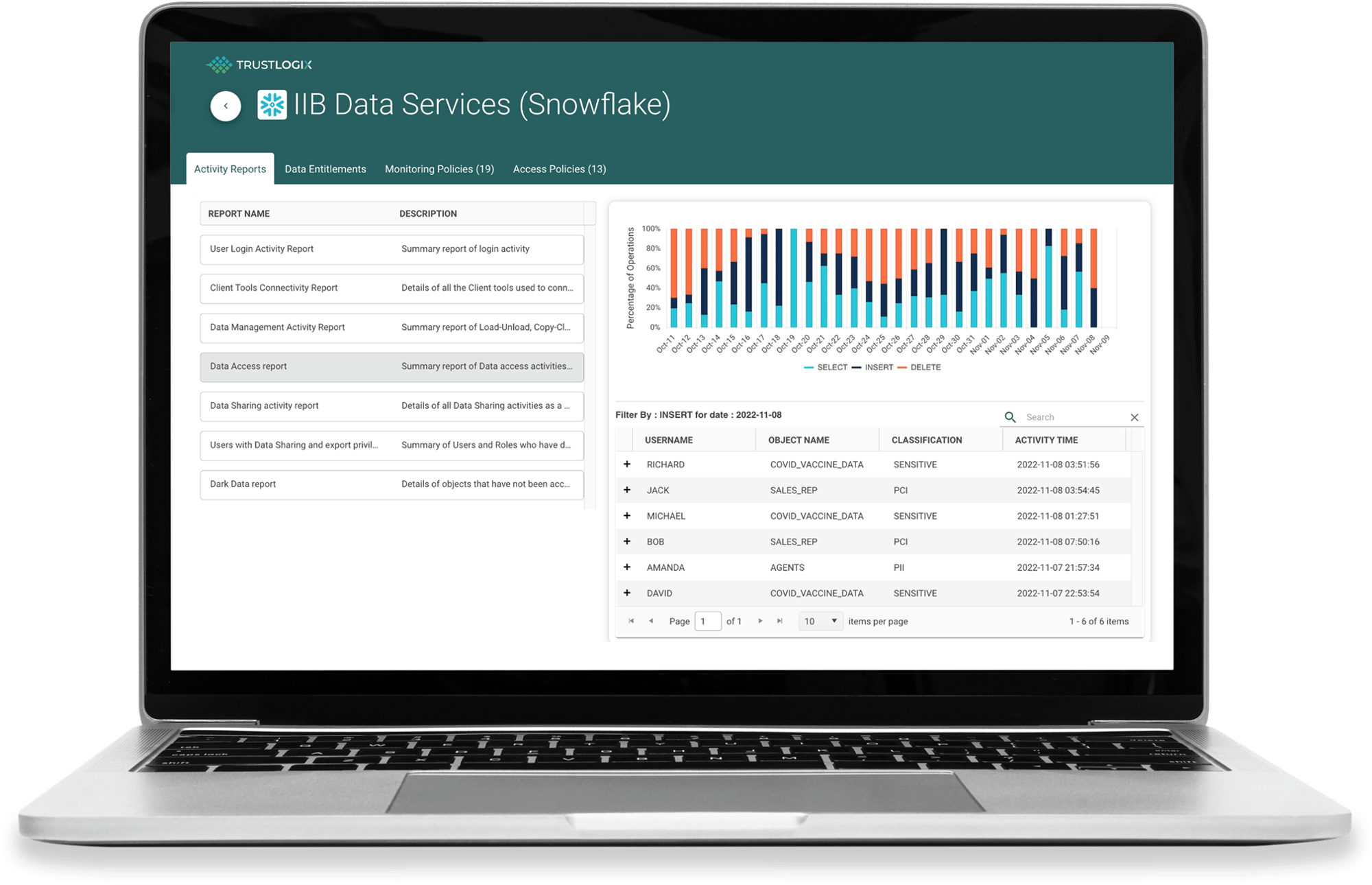
Data-Centric Audit Reporting Ensures Security and Compliance
Quickly and easily produce comprehensive audit reports regarding sensitive data for various regulations and legislative mandates including SOX, GDPR, HIPAA, and PCI.
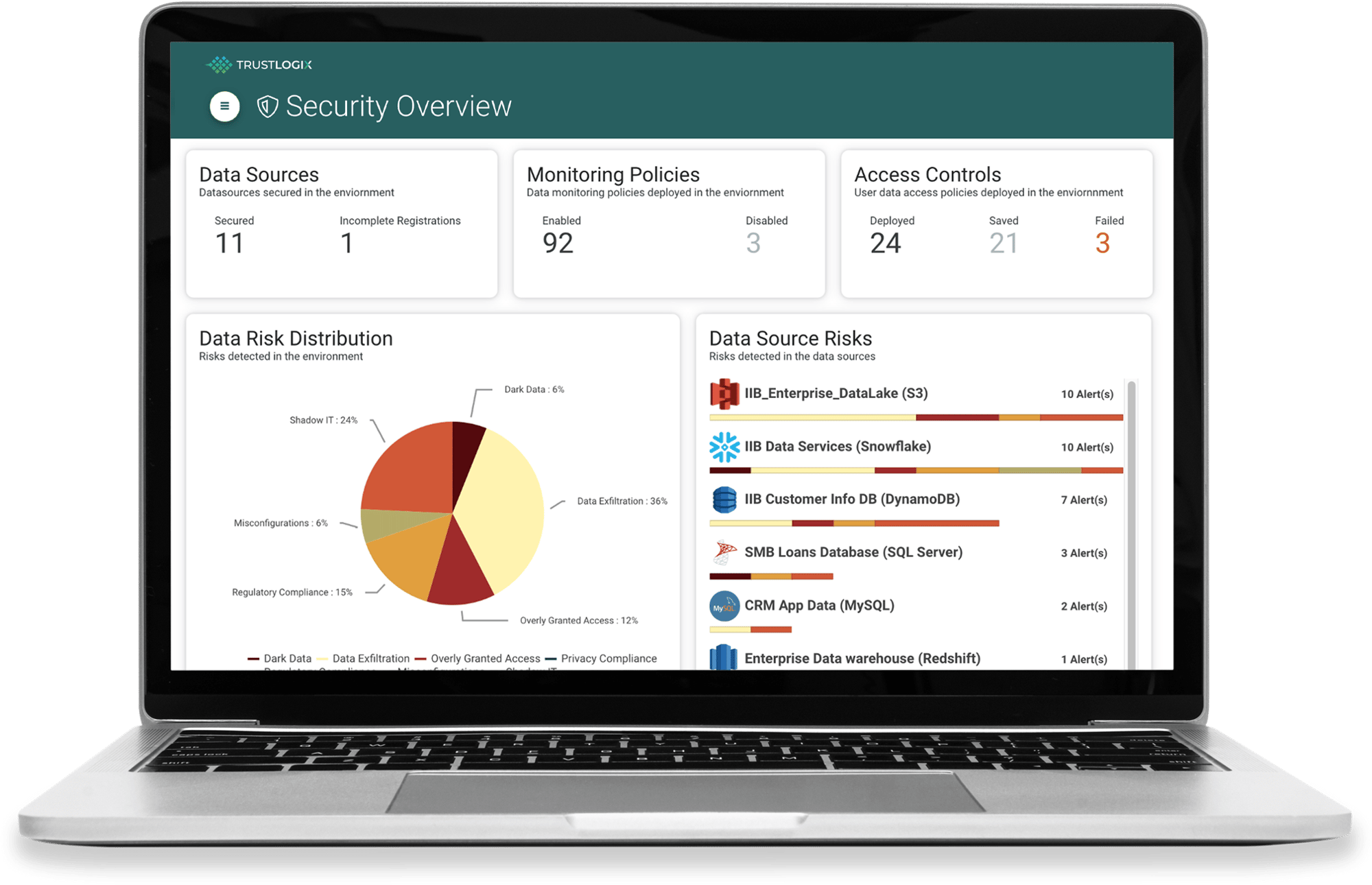
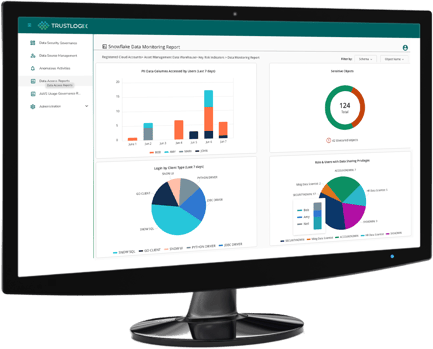
Data Risk Dashboard
Alerts
Recommendations
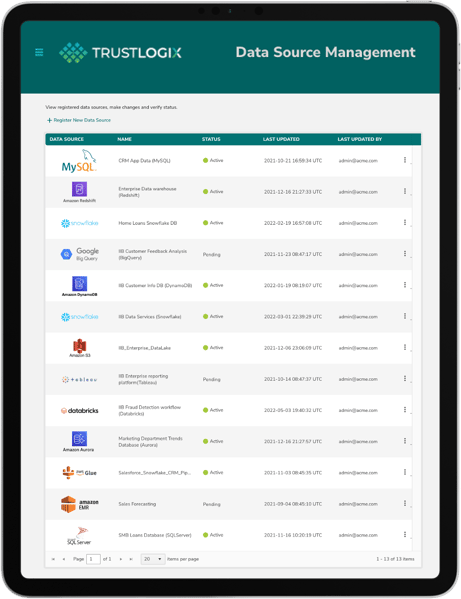
Data Entitlements
Automated Access Policies
Audit Reports
KEY BENEFITS OF TRUSTLOGIX
Your Data Stays Private
Proxy-less, agentless architecture ensures that we never touch your data
No Vendor Lock-in
Zero proprietary integrations into your applications or data platforms
Flexible Deployment Models
TrustLogix can run as a pure SaaS solution or be deployed into your private cloud
Blazing Performance
At runtime, there is zero overhead between your authorized users and your data
Visibility
Centralized data access and usage monitoring across all clouds
Actionable Insights
AI-driven recommendation engine provides personalized suggestions to tighten your data access policies
Compliance Reporting
Rich evidence to support your SOX, HIPAA, GDPR, PCI, and other legislative mandates
Granular and Precise Data Entitlements
Attribute-based access control (ABAC), role-based access control (RBAC), and fine-grained data controls secure the entire data pipeline—from ingestion to usage
No-Code Policy Administration
TrustLogix auto-generates the underlying SQL code for Snowflake, Redshift, S3, Databricks, and your other cloud data platforms to ensure easy, fast, and consistent policy management
Re-certification
Remove access when it's no longer needed to ensure continuous enforcement of the Least Privilege principle
Data On-Demand
Reduce the data request/approval/access process from weeks down to minutes
Business-Aligned
Streamline HIPAA, GDPR, PCI, and SOX compliance by leveraging business data tagging from Collibra, Snowflake, and others
Business-Security Collaboration
Empower business and security teams to efficiently collaborate to define and enforce data access policies
.png?width=512&height=500&name=Zero-Risk%20(professional).png)
Secure Data Access Easily Integrates with Top Cloud Providers
Don’t worry about the specific provider policies. Simplify your cloud data security management from a central SaaS platform using AI and automation.



Secure Data Access Use Cases
discover hidden data risk
Analyze access patterns and user behavior to uncover hidden risk caused by ineffective controls, forgotten data, and overly permissioned access.
streamline data secops
Leverage TrustLogix’s Role Navigator to manage complex data access policies and quickly troubleshoot and resolve access issues.
Simplify Multi-Cloud Audit & Compliance
Demonstrate compliance with GDPR, HIPAA, PCI, SOX, and other regulations across all your disparate cloud data stores with speed, ease, and simplicity.
Enforce Least Privilege Policies
Shave down access to your data to what is truly needed using RBAC, ABAC, and Data Entitlements for data consumers and privileged users.
Govern Multi-Cloud Data Sprawl
Track your data as it proliferates from across disparate clouds, and get alerted for suspicious behavior and indicators of exfiltration.
Accelerate LOB Onboarding
Leverage your existing access patterns to onboard Lines of Business (LOBs) faster using organization-wide role and privilege templates

