Data Secured.
AI Unleashed.
Secure Snowflake Data & Deploy AI with the Leading Data Security Platform.
Enterprise-Grade Security for Snowflake

Streamline Access
Governance
Inventory users, roles, and access paths for full visibility of data access, while enabling flexible policies, federated control, and secure data sharing in Snowflake environments.

Securely
Deploy AI
Govern access to sensitive training data and AI agent inputs based on user role, purpose, and project scope—ensuring secure and compliant AI deployment within your Snowflake environment.

Mitigate Data
Access Risks
Continuously monitor Snowflake data to detect misconfigurations, policy violations, and exfiltration risks— ensuring continuous audit-readiness and enabling remediation of access issues before they turn into incidents.





Learn how a leading Fortune 500 healthcare organization achieved 50% faster data access through self-service, no-code provisioning with TrustLogix.
Key Capabilities to Secure Your
Snowflake Data and Unleash AI
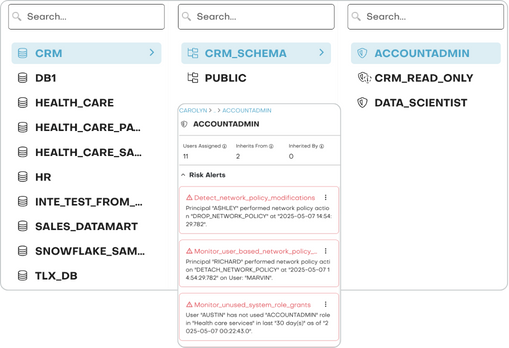
Data Access Visibility and Governance
Inventory users, roles, and access paths.
Define and enforce flexible access policies with a no-code policy builder.
Achieve consistent access governance at scale through federated policy management.
Security for Cortex AI
Secure AI/ML workflows by controlling access to models and training data.
Apply access controls and monitor sensitive content in Cortex Document AI.
Enforce real-time oversight and guardrails for Cortex Agents.
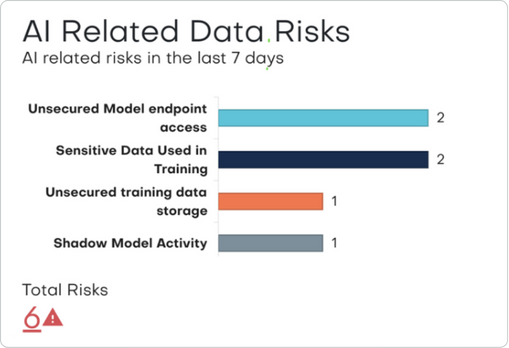
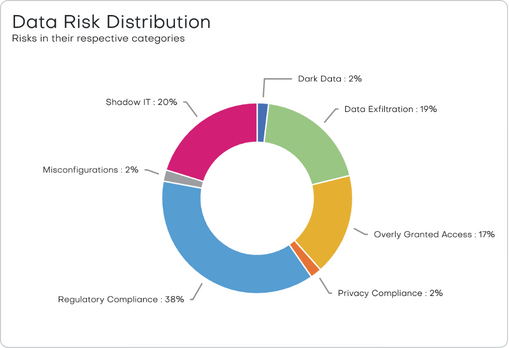
Risk Detection and Posture Management
Uncover dark data, overprivileged access, misconfigurations, and shadow IT.
Monitor and secure Snowflake network traffic with policy recommendations.
Monitor and control Snowflake data sharing across accounts and external partners.
Continuous Compliance and Audit Readiness
Alignment with regulatory frameworks - HIPAA, PCI DSS, GDPR, and DORA.
Continuous monitoring, policy enforcement, and automated audit reporting.
Real-time violation response and ensuring governance of sensitive data.
Resources
See How TrustLogix Secures
Snowflake Environments
Protect sensitive data, govern access intelligently, and accelerate compliance initiatives across your
Snowflake cloud environment — with no disruption to scale or performance.



