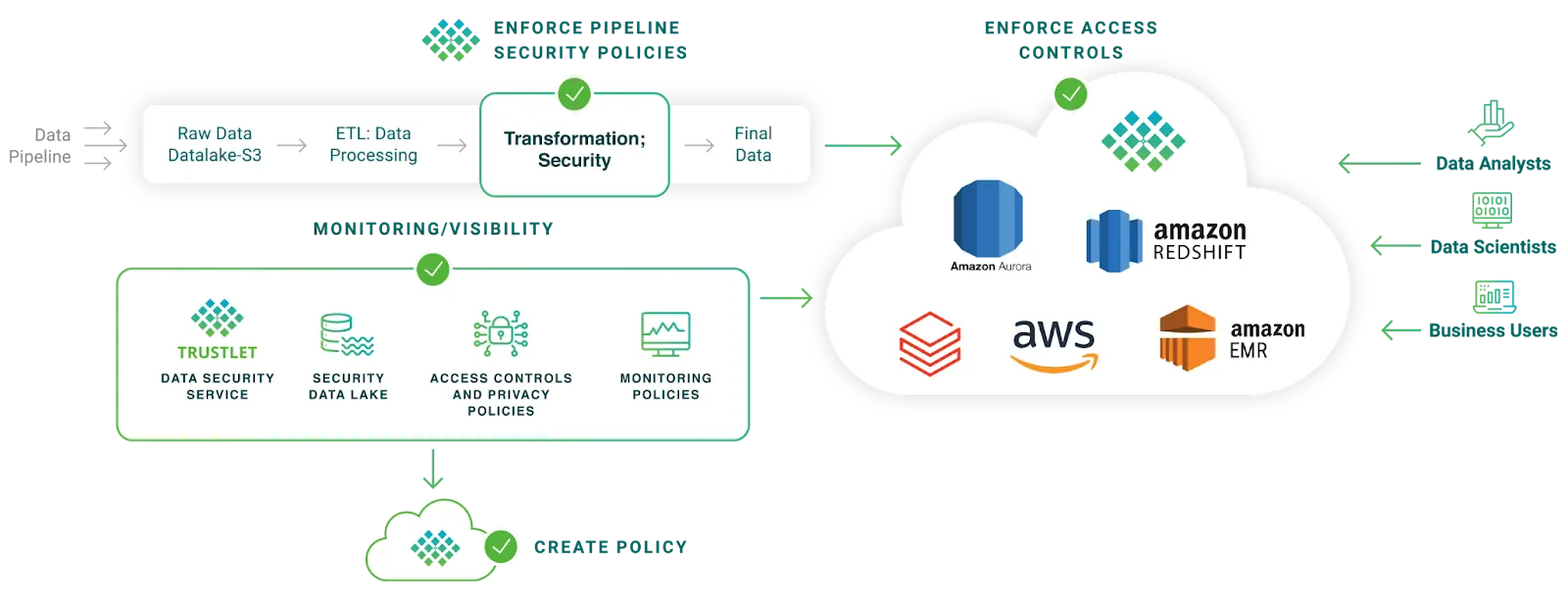
Unified Data Security Across AWS Redshift, S3, and RDS
TrustLogix brings centralized governance and identity-aware policy enforcement to your AWS data services. Whether you’re storing structured data in Redshift, unstructured files in S3, or transactional records in RDS, TrustLogix delivers fine-grained access control, visibility, and compliance without slowing down performance.
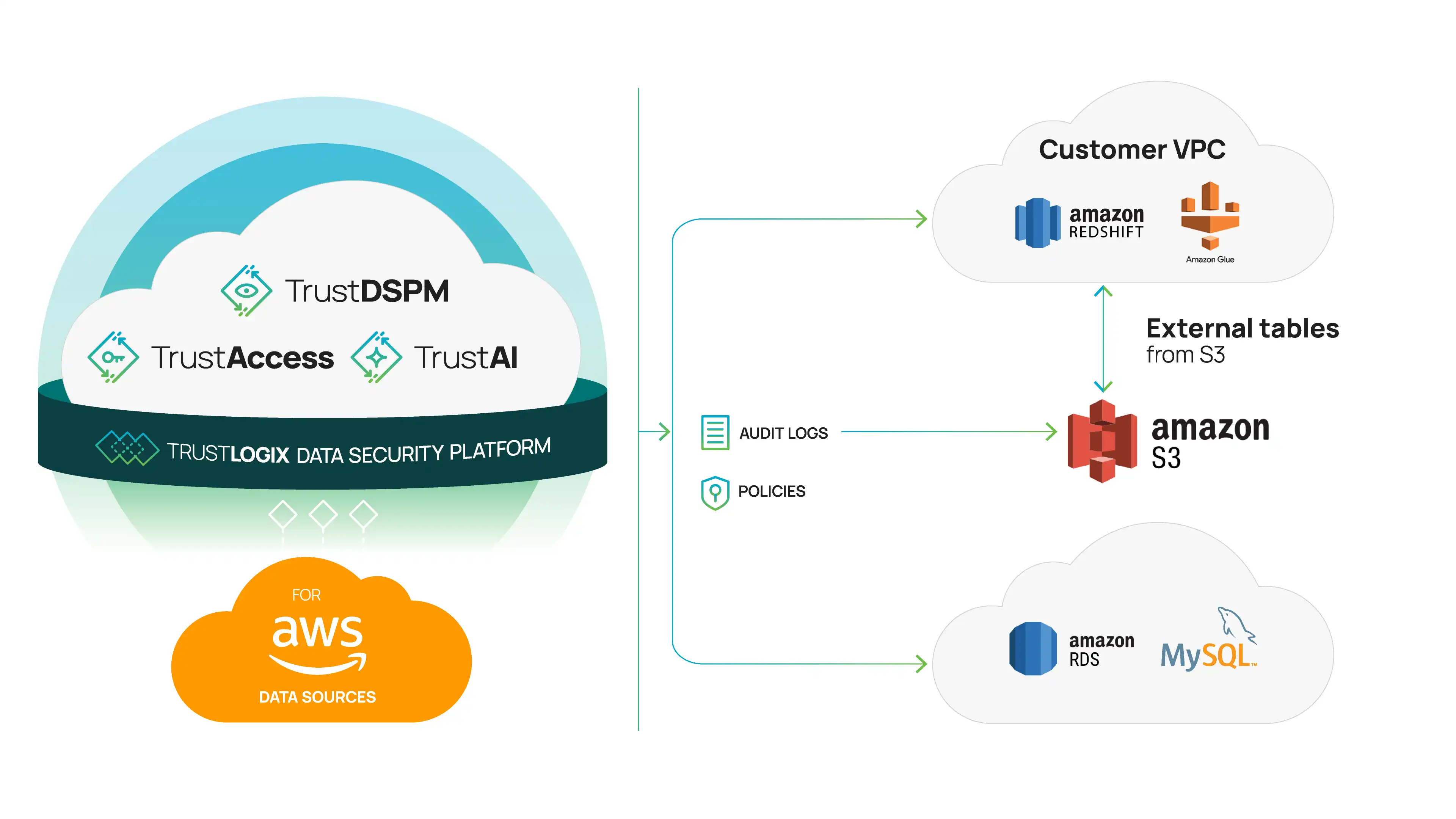

Why AWS Customers Choose TrustLogix
One unified control plane for access policies across Redshift, S3, RDS, and beyond
Real-time visibility into entitlements, activity, and risks—no agents required
No-code policy creation that works with your existing IAM model
Fast to deploy, easy to scale—see insights within minutes
Account-based pricing for flexible adoption across business units
Redshift: Secure Analytics at Scale
Bring consistent, policy-based access controls to your Redshift environments—without interrupting your analytics workflows.
- Enforce least-privileged access for Redshift data by user, role, or job function
- Align data access with business context and compliance requirements
- Monitor usage patterns to detect and remediate risky or unused entitlements
- Centralize policy governance across Redshift and other AWS services
- Avoid manual IAM configurations with no-code policy creation

S3: Control Access to Unstructured Data
Apply consistent governance to sensitive files stored in S3—no matter how fast your data grows or how widely it’s shared.
- Monitor access to unstructured data across buckets and services
- Visualize data access patterns and policy violations in real time
- Define and enforce policies that reflect business context, not just bucket-level roles
- Reduce reliance on complex IAM and bucket policy configurations
- Govern S3 alongside Redshift, RDS, and downstream analytics tools

RDS: Visibility into Who Accesses What—and Why
Unlock visibility into database-level access activity across Amazon RDS.
- Track access by identity, time, and purpose—even without native logging
- Identify excessive or unnecessary entitlements to reduce risk
- Enforce policy-based controls without altering RDS operations
- Bring database access into your centralized governance model
- Support security, audit, and compliance requirements across cloud-native and legacy workloads
A leading financial institution used TrustLogix to unify governance across Redshift, RDS, S3, and Snowflake—reducing time-to-value for secure data access from days to minutes while eliminating policy drift and manual audits.


Find us in the Amazon Marketplace
Experience TrustLogix in Action
Schedule a call to discover how TrustLogix can accelerate your AI initiatives with faster, safer data access.