Cloud services like Snowflake, Amazon Redshift, and Databricks have enabled enterprises to diversify...
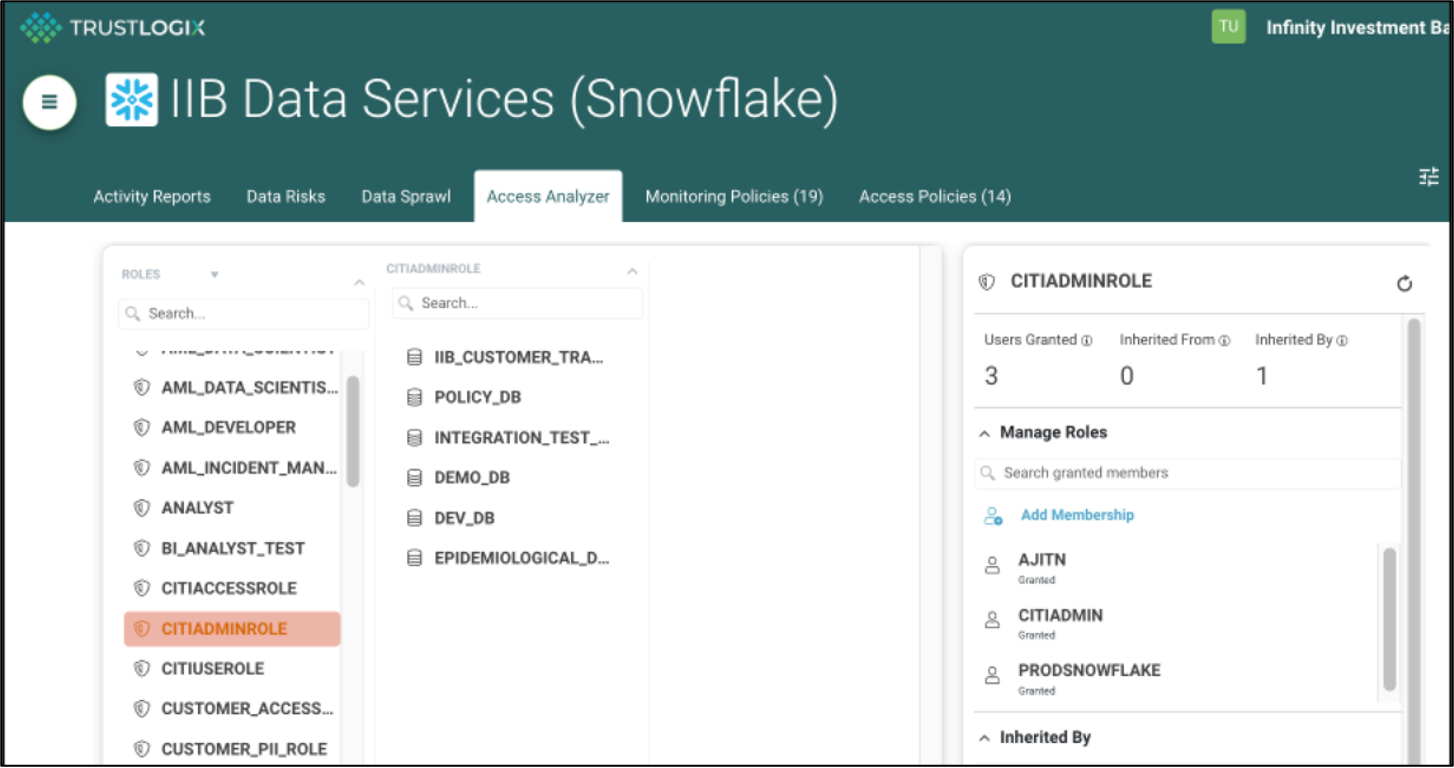

Cloud services like Snowflake, Amazon Redshift, and Databricks have enabled enterprises to diversify...

AWS re:Invent was a terrific event as always, and once again there was a flood of announcements rega...

October is Cybersecurity Awareness Month, and TrustLogix is proud to partner with the National Cyber...
Earlier this summer, Amazon announced Redshift RLS (Row Level Security) , a rich new set of capabili...

A common question we hear in first meetings with new customers is “If I already have a Data Catalog ...
Data Access Governance is an important part of any organization’s IT strategy. It ensures that only ...

Security practitioners are all too familiar with the concept of role explosion or role proliferation...

Data is being created today at speed and scale that we’ve never seen before. Spurred on by the promi...
As companies continue to generate massive amounts of data on a daily basis, classifying and securing...
LEARN MORE ABOUT HOW WE CAN HELP YOU