TrustLogix Data Security Tool Integrates with Snowflake Architecture
Stay in the Know
Subscribe to Our Blog
TrustLogix delivers insights into data misuse and detects unprotected data that helps businesses proactively control access and implement Least Privilege security model
TrustLogix has worked closely with the Snowflake team on this integration architecture. We'd like to acknowledge Paul Gancz, Partner Solutions Architect at Snowflake for his valuable contributions to this blog.
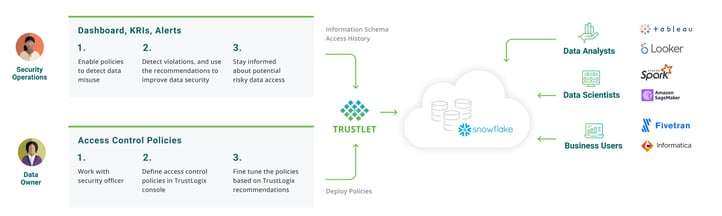
Organizations are transforming their business processes, culture, and customer experiences to rely more on digital technologies to achieve better business outcomes. Data is the critical part for each of these digital transformations. In many cases this involves PII (Personally Identifiable Information) or other sensitive data, which brings a need for oversight on how this data is used. Furthermore, regulations, compliance, and security controls can create conflicts between business teams and data security operations. A cross-team strategy is required to reduce the friction between these teams. Data security operations require a platform that serves as an accelerator to data-led innovation without impeding the process. The platform should:
-
Provide the governance team with visibility into who is accessing data
-
Give the data security team a unified console to create consistent data security policies across multiple data platforms
-
Make it easy for data consumers such as Analysts, Data Engineers, and Data Scientist to get immediate access to the data to which they are entitled
Discover Data Access Issues
Governance and compliance teams require visibility into who is accessing data. They need to be alerted if any data access violates compliance policies such as SOX (Sarbanes-Oxley), SOC2, GDPR, etc. TrustLogix furnishes a library of policies to monitor user and data activity in Snowflake to help them. It also provides alerts when there is any deviation from the organization's established security rules. Additionally, TrustLogix flags other Key Risk Indicators such as:
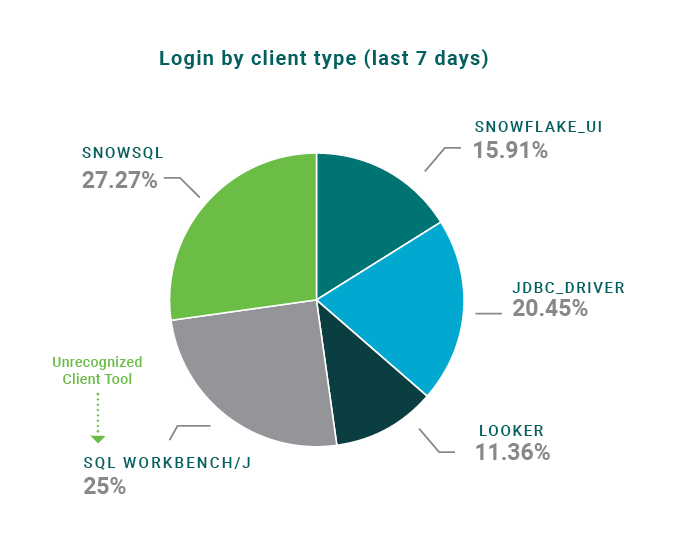
- Identify Shadow IT tools used to connect to Snowflake or unexpected geo-locations used
to log into Snowflake. For example, in the diagram below “ SQL Workbench/J” is not an approved IT tool - Alert when users export sensitive data into AWS S3 buckets
- Alert when sensitive data is shared between accounts
TrustLogix analyzes data in Snowflake’s Account Usage views, Access History, and Session tables to derive these insights.
Recommendations to Enforce Least Privilege Access
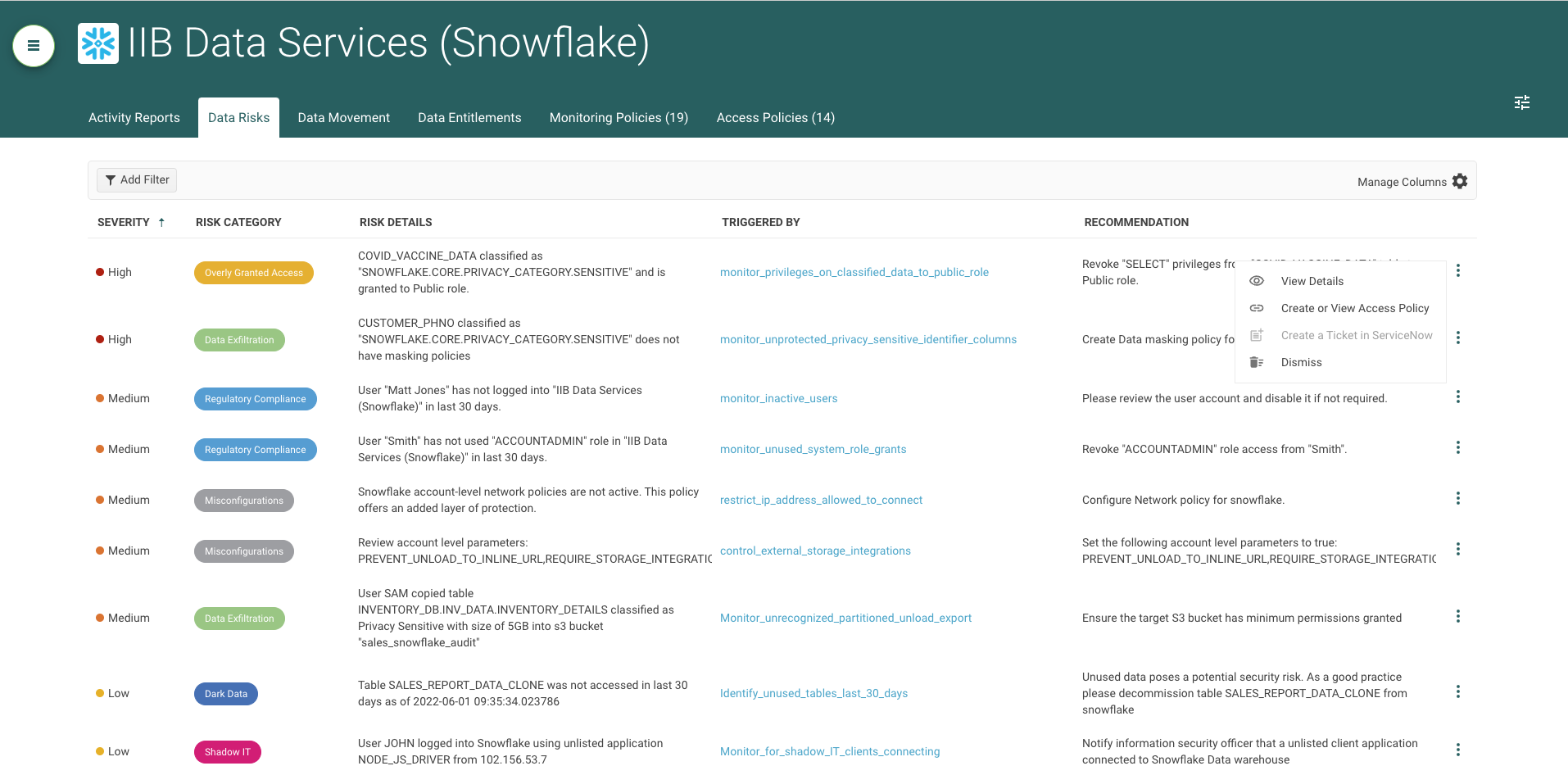
Data owners are required to establish a Least Privilege Access model for their data in Snowflake and other cloud data platforms. TrustLogix analyzes various Snowflake data security policies, audit logs, and identity and roles assignments to detect possible deviations from industry best-practices for the Least Privilege model, and offers actionable recommendations such as:
-
Privileged User Activity: Recommendations-based analysis of user activity. Some users have roles or permissions that give them access to privileged operations like Export/Import Copy/Duplicate sensitive data. TrustLogix analyzes the Snowflake Access History View to detect anomalies & provides recommendations
-
Overly Defined Privilege Assignments: Analyze privileges granted to a role and compare with access logs to determine which privileges are least used. Offer recommendations to modify the policy to adhere to the principle of Least Privilege
-
Data Security Policy Effectiveness: Use access patterns to understand the level of policy effectiveness on classified data objects. Provide recommendations based on usage patterns. Example: Un-protected or publicly granted Sensitive Data Objects
Read More: Birthright Data Entitlements: Secure Your Data as It's Born
Define and Enforce Data Access and Entitlement Policies
Data owners require the power of fine and coarse-grained Access Control on data to satisfy compliance regulations, internal business mandates, and basic security principles.
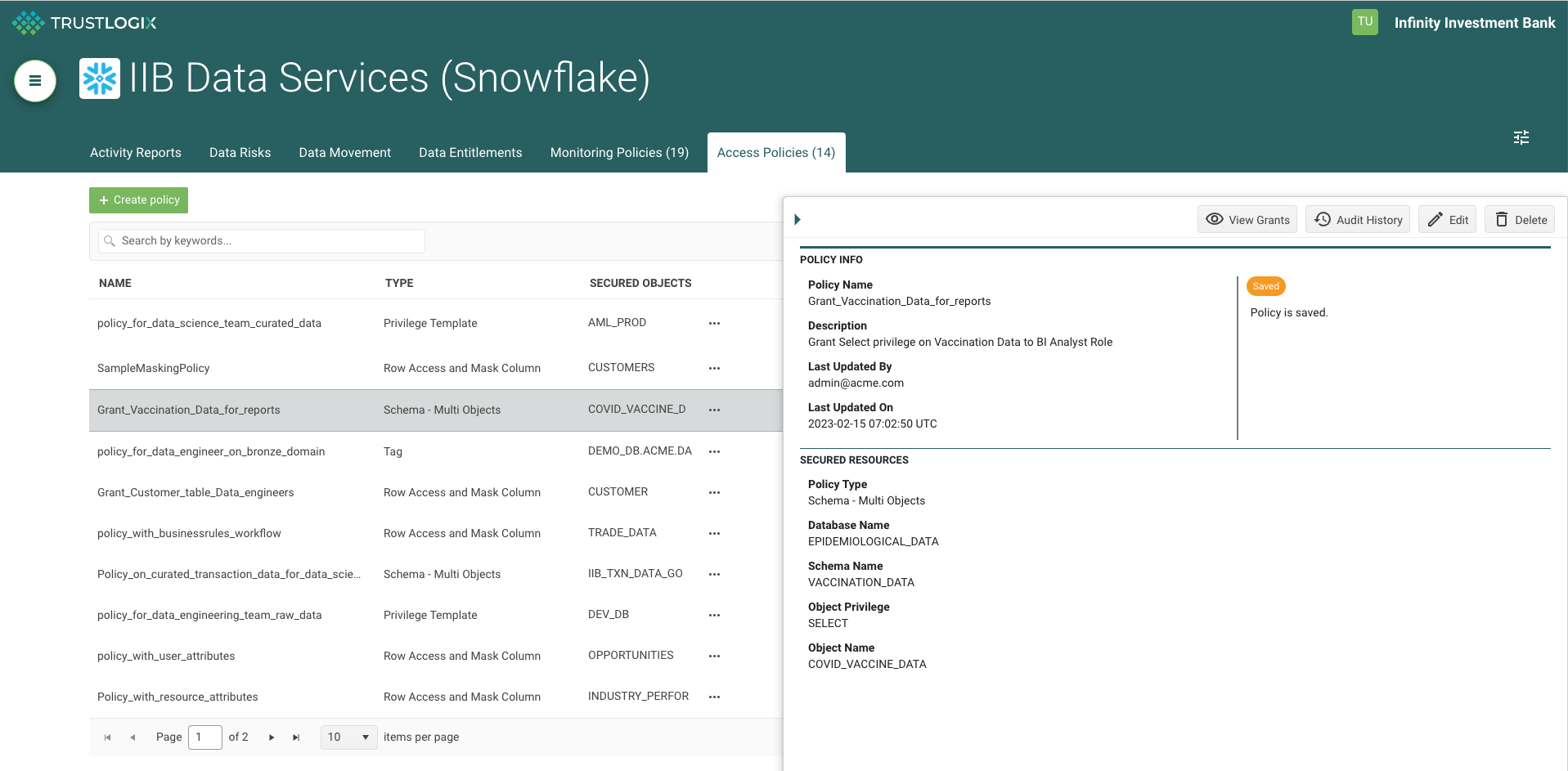
Snowflake provides customers with Row Access policy, Conditional Masking, Dynamic Data Masking, and Tagging capabilities. TrustLogix leverages Row Access Policies and Dynamic Data Masking capabilities to deliver a simplified UI console for data owners to build high-precision data security policies.
TrustLogix also complements Snowflake’s native data security constructs by providing business entitlements based on fine-grained data security. Organizations typically have externalized business entitlement policy data that is required to determine what data a user is entitled to.
For example: In a publicly traded company, users in the marketing organization cannot view financial data for the current quarter. In this scenario, TrustLogix integrates with the external business policy and converts it into the appropriate Snowflake native policy.
Summary
With the TrustLogix solution, data owners, data engineers, data governance practitioners, and data security officers gain visibility into data misuse discover data access and sharing patterns, and enforce access control policies with an easy to use policy console and scalable cloud-native Trustlet architecture.
