Deliver secure and compliant
AI projects at scale
with Databricks and TrustLogix
Speed and oversight are critical components of successful AI projects.
- Fine-grained access controls at scale
- Data security posture management designed for Databricks

Why trustlogix?
Hear from Steve Zalewski, former CISO of Levi-Strauss & Company, on how TrustLogix solves the critical needs of today's data and security teams.
BRING AI TO YOUR DATA AND DELIVER AI PROJECTS QUICKLY AND SECURELY WITH DATABRICKS AND TRUSTLOGIX
Facilitate secure and compliant AI projects while accelerating security approvals and automating access controls for enterprise-wide data.
Problem Statement
- As a data security team lead, how do I know if my IT teams are following Databricks security best practices?
- What new data assets are coming in and what data is leaving?
Solution Statement
TrustLogix provides a Data Security Posture Management service designed for Databricks.
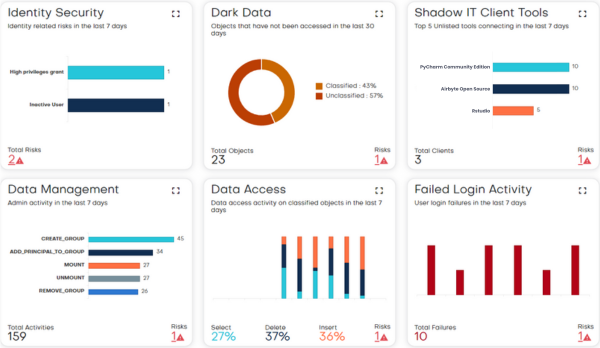
TrustLogix continuously monitors the Databricks cluster to gain visibility into various data risk categories, including:
- Dark data risks — identifying unused data left unclassified or unprotected
- Data exfiltration risks — detecting abnormal data access or transfers
- Overly granted access risks — finding improper user permissions and entitlement creep
- Regulatory compliance risks — spotting configuration gaps against frameworks like HIPAA and PCI
- Shadow IT risks — discovering unsanctioned tools that connect to Databricks
- Misconfiguration risks — pinpointing security policy gaps or flawed settings
TrustLogix analyzes these risks to provide actionable intelligence for securing data within Databricks clusters. The solution integrates directly with Databricks to provide automated access discovery risks and continuous insights into their security posture across multiple risk factors.
Problem Statement
- I am the Head of the Enterprise Data Platform Team and my business teams are creating multiple Databricks clusters, and modernizing the data ecosystem by leveraging data architectures like data mesh and data fabric. How do I ensure data authorization is managed at scale for all users?
Solution Statement
TrustLogix provides centralized governance capabilities to efficiently manage authorization across this sprawling landscape. Its cloud-native architecture integrates seamlessly with Databricks to provide a single pane of glass for enforcing and auditing entitlements consistently across all your Databricks accounts and clusters, regardless of location.
TrustLogix integrates with Databricks Unity Catalog’s governance capabilities like tagging to manage data products at scale.
Additionally, TrustLogix's delegated administration capability can help decentralize policy management but still maintain central visibility
Problem Statement
- I am a data owner - my business data needs to be secured using complex business rules. We need policy-based authorization that depends on unique combinations of organizational permissions, job role, and purpose for accessing data
- We need to ensure the jurisdictional policies are enforced on data based on state and national laws that govern the data.
Solution Statement
TrustLogix empowers you to define and enforce intricate business rules for securing access to your sensitive data assets. With TrustLogix's fine-grained attribute-based access control (ABAC) capabilities, you can implement sophisticated policy-based authorization that leverages Databricks native row filtering and unity catalogs for unique combinations of organizational permissions, job roles, and the purpose for accessing the data. This ensures that only authorized personnel can view or manipulate your data based on their real-world roles and intended use.
Moreover, TrustLogix allows you to map and layer jurisdictional policies on top of your business rules. It provides controls to restrict data access based on state and national data residency laws governing where your data resides. This safeguards you from inadvertently violating compliance regulations across the various geographic locations where your business operates. With TrustLogix, you gain centralized visibility and control to efficiently author, deploy, and maintain an enterprise-wide data security policy fabric customized to your unique risks and requirements.
Through its no-code policies, TrustLogix allows you to define and deploy attribute-based access controls mapped to your organization's roles, responsibilities, and compliance requirements. These policies automatically propagate to secure data access across your distributed data domains, fabrics, and meshes without scripting.
Problem Statement
- I am the business owner. I want to monetize my data by leveraging open data sharing for data, analytics, and AI by Databricks. I want to build secure data clean rooms to collaborate with data partners. How do I ensure the data my teams are sharing is sanitized and does not have any PII or enterprise proprietary data?
- How do I ensure data shared is compliant with the SLAs and with current regulations?
Solution Statement
TrustLogix lets you manage data-sharing privileges and get full visibility on what data you are consuming and sharing with outside organizations.
TrustLogix simplifies the provisioning of data-sharing policies with a few clicks. Visualize your data flows, and alert and resolve any risky sharing of sensitive data
Integrate with Databricks Unity Catalog and Tagging to identify sensitive data, and protect with no-code Databricks-native de-identification and access policies.
Bring AI to your data projects with Databricks and TrustLogix!
TrustLogix is SOC2 Type 2 Compliant, uses no agents or proxies, requires read-only metadata access, and does not see or touch the data itself
