DATA PROTECTION
SIMPLIFIED FOR EVERY ROLE
Scale security. Simplify policy enforcement. Deliver data on-demand.
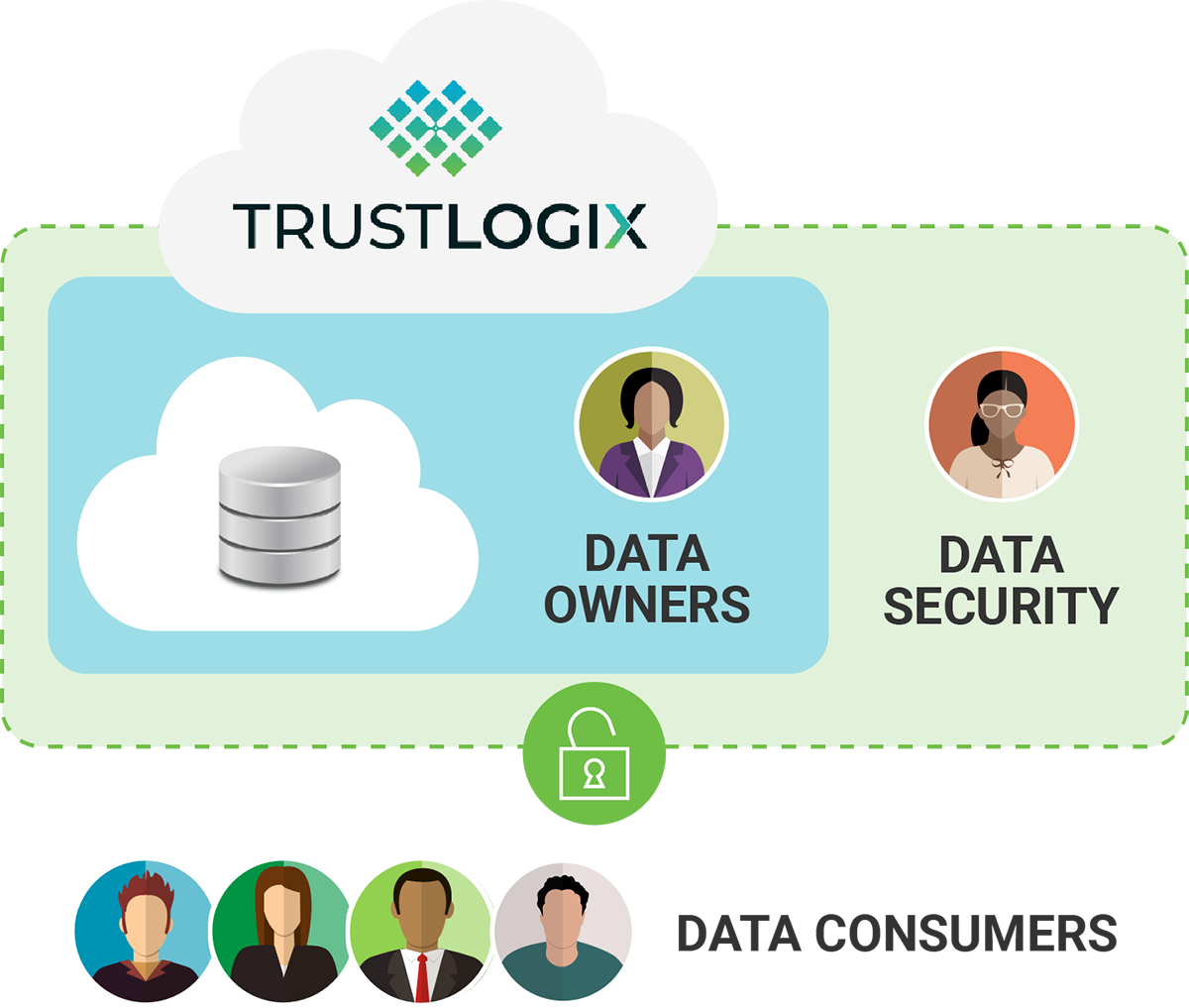
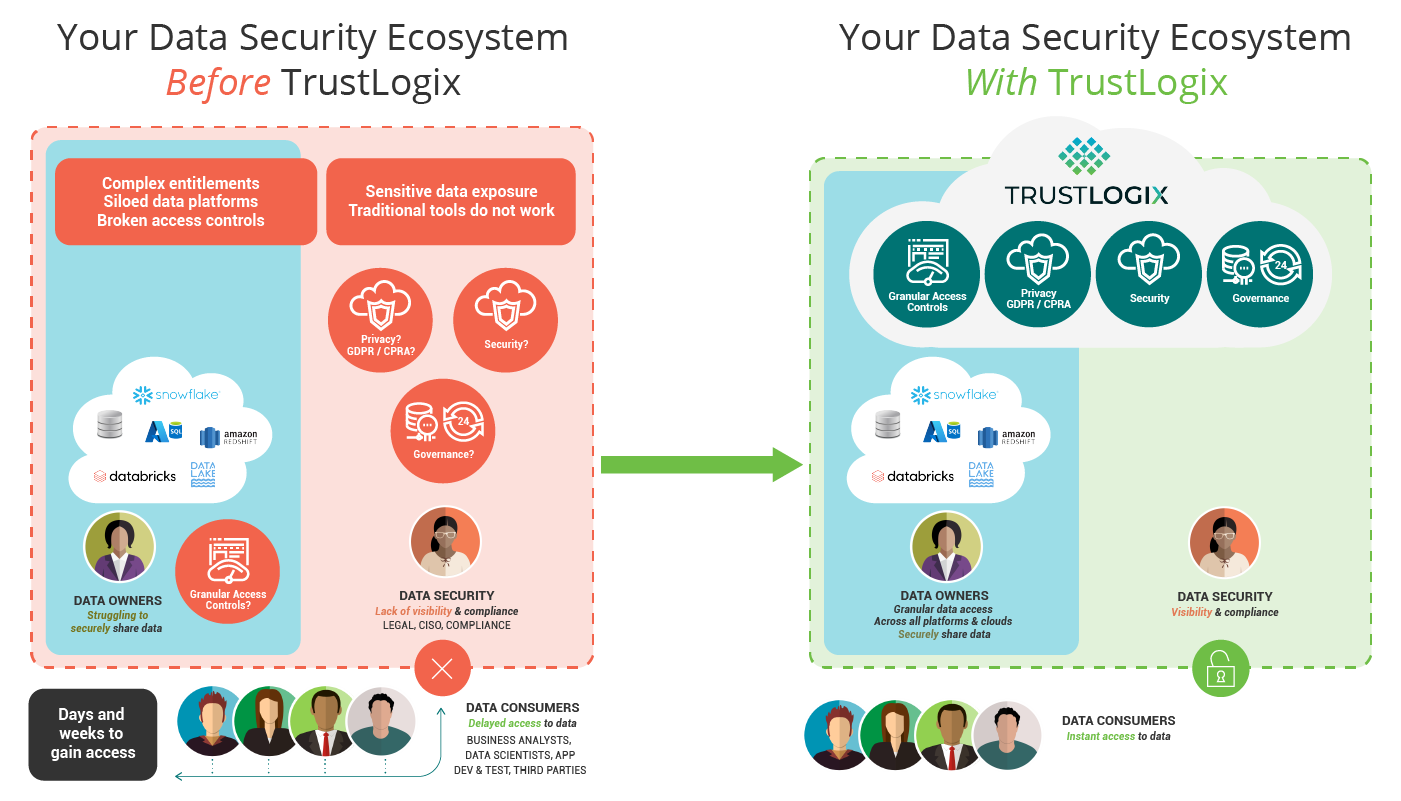
Enterprise Data Protection is Massively Complex Across Clouds.
It Doesn't Need To Be!

Data Owner
The Problems: |
With TrustLogix You Get: |
| Overprivileged accounts |
Exactly what consumer needs |
| Unknown data privacy violations |
Visibly compliant, instant alerting |
| Row- and column-level limits |
Fine-grained role-based and attribute-based access controls |
| Operational overhead |
Streamlined collaboration with security & consumers |

Data
Security
Owner
The Problems: |
With TrustLogix You Get: |
| Ghost accounts |
Ongoing account audit & control |
| Dark data & data sprawl |
Data only where it is needed |
| Noncompliant data share & copy |
Visibly compliant, instant alerting |
| Shadow IT usage |
Block unauthorized clients |
Data
Consumer
The Problems: |
With TrustLogix You Get: |
| Blocked by incorrect security policies |
Fine-grained policies, get exactly the data needed |
| Wait many days for approvals |
Same day / rapid response |
| Missing business deadlines |
Data access as fast as needed |
LEARN MORE ABOUT HOW WE CAN HELP YOU
