
TrustLogix for Amazon Relational Database Service (AWS RDS)
Secure, Govern, and Audit Transactional Data Access in AWS RDS
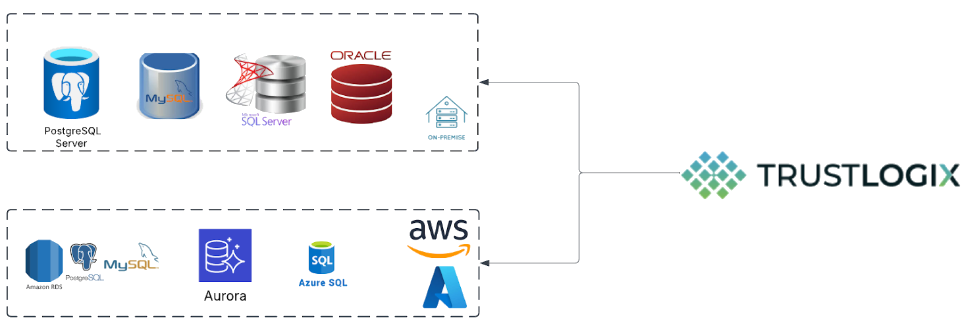
TrustLogix helps organizations secure sensitive data, enforce least-privilege access, and meet compliance requirements across all RDS instances with intelligent monitoring and automated access governance.
Visibility and Control Over Data Access
Understand and manage data access risks with actionable insights and real-time audit trails.
Transactional databases managed under RDS often contain live, business-critical data, making unauthorized access or breaches especially damaging. Comprehensive logging and real-time monitoring are essential for compliance, incident response, and forensic investigations.
End-to-End Visibility
TrustLogix provides a centralized view of access across all RDS instances, including detailed mapping of role hierarchies and user entitlements to identify over-privileged accounts. It visualizes how data is accessed, moved, and backed up, while Dark Data Reports surface unused or forgotten data that could increase risk.
Audit-Ready Access Controls
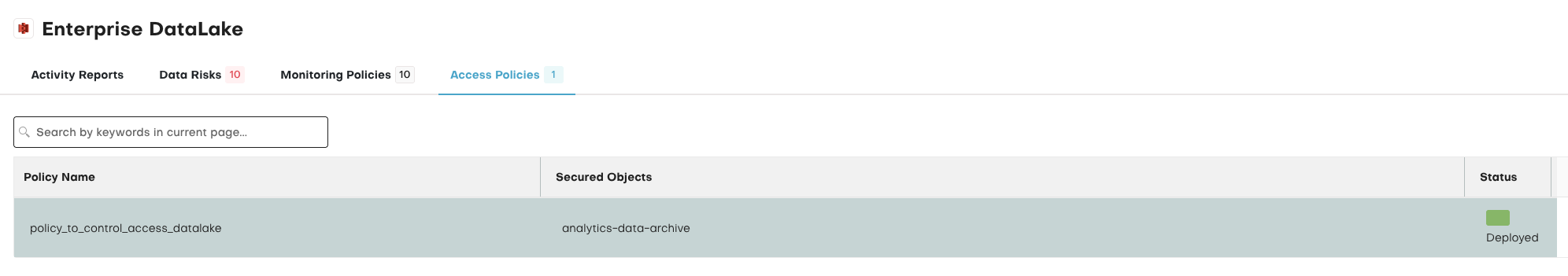
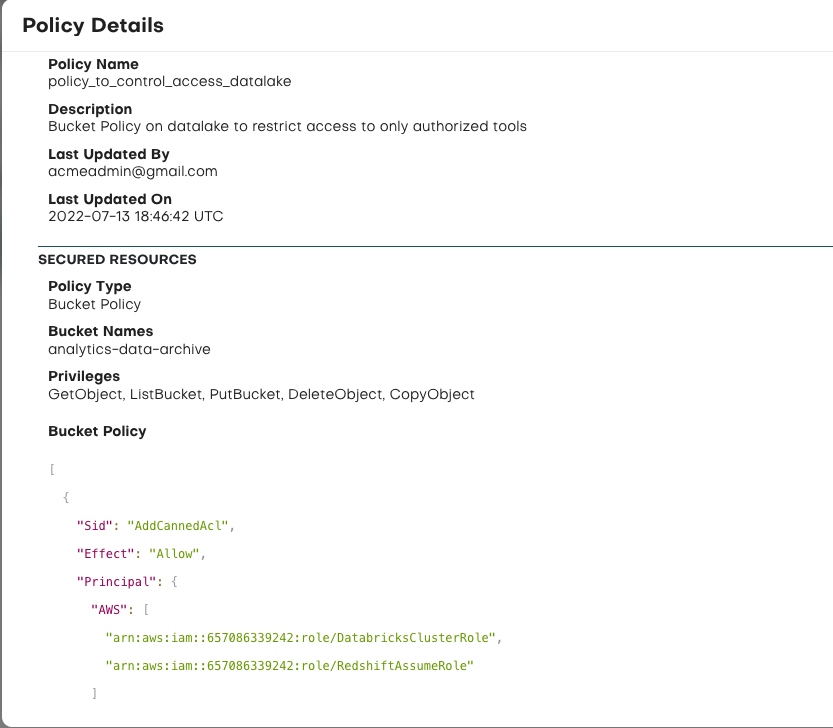
The platform monitors for sensitive data being copied between environments, such as from production to QA or dev—a common DORA violation. With full activity logging, asset tagging, and data sprawl tracking, TrustLogix helps teams maintain control and generate clear, auditable evidence of proper access governance.
Risk Reduction and Compliance Enforcement
Enforce granular access controls across all RDS instances to reduce risk and consistently meet security, privacy, and compliance requirements
Transactional databases demand precise access policies to prevent over-permissioning and enforce least-privilege principles. This is essential to reduce exposure of sensitive data like PII or financial records.
Service Account Protection
TrustLogix actively monitors service accounts—often the source of unintended risk—for signs of misuse, including interactive logins or suspicious data access patterns. Alerts are triggered in real time to help contain threats before they escalate.
Compliance Enforcement
To support frameworks like PCI DSS, HIPAA, GDPR, SOX, and DORA, TrustLogix enforces the principle of least privilege to ensure only authorized users and third parties can access sensitive data. It continuously audits for violations across complex, multi-cloud environments—helping teams maintain compliance posture and pass audits with confidence.
Automated Data Access Governance and Incident Response
Automate data access governance and incident response with continuous monitoring for misconfigurations, access anomalies, and risky service account activity across hybrid environments
Persistent credentials used by applications and service accounts pose significant security risks, including the potential for misuse, privilege escalation, or lateral movement within environments. Strong governance is needed to monitor and restrict how these identities interact with data.
Automated Data Access Governance
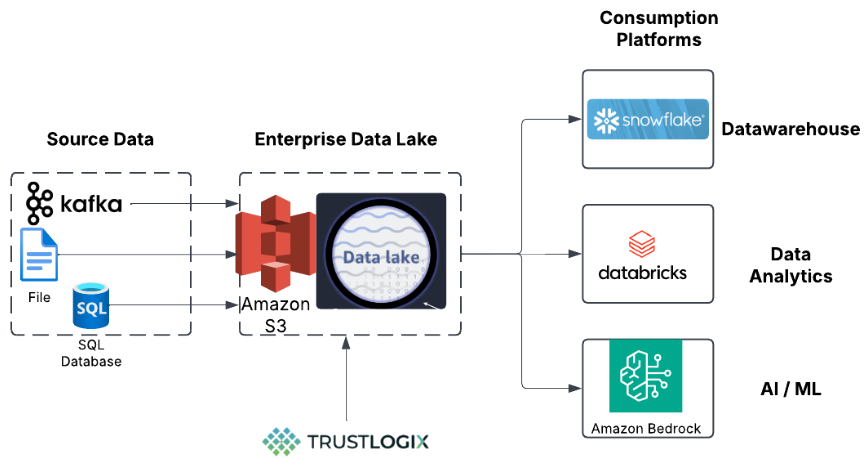
TrustLogix automates data access governance at scale by continuously scanning for access anomalies, misconfigurations, and compliance gaps across hybrid environments, delivering these capabilities as a unified Data Security Posture Management (DSPM) platform. It tracks how data is used and moves across environments, offering proactive policy recommendations to tighten controls without manual oversight.
Incident Response
TrustLogix strengthens incident response by monitoring persistent credentials and service accounts for unauthorized or anomalous behavior. This enables teams to contain risks quickly, maintain visibility into account activity, and provide the audit evidence needed during and after an incident.
Democratize Data Security to
Accelerate Business Innovation Across AWS

AWS Services supported












