Achieve Least-Privilege Access for All Your Data
Gain enterprise-wide control over data with unified access governance that simplifies complex role hierarchies and enforces least-privilege access at scale. TrustAccess accelerates data analytics projects by extending consistent access controls from source to dashboard across Snowflake, Databricks, and Power BI. Using an intuitive, no-code policy builder, data owners can define sophisticated policies that align with business requirements, while security teams maintain centralized oversight and data teams streamline approvals—driving agility and enabling faster, more secure access to data.
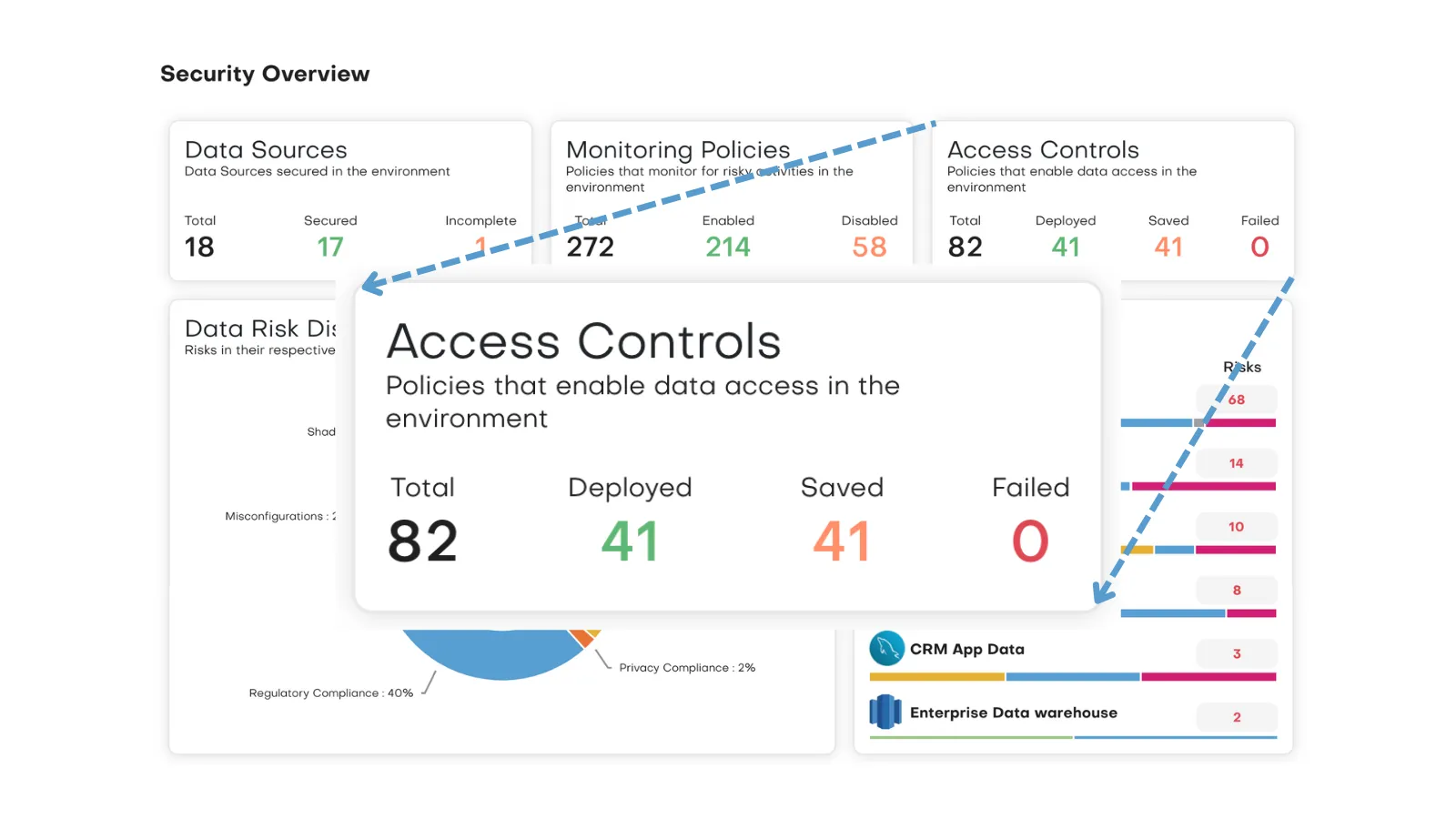
Control Data Access Everywhere
Unify and Enforce Consistent Policies
Align users with functional roles and eliminate tangled, overlapping permissions to streamline your path to least privilege. Maintain consistent rules across data platforms and Microsoft Power BI to reduce complexity and prevent privilege drift.
Accelerate Data Projects with No-Code Policies
Create fine-grained access policies by user, role, geography, or purpose in minutes—using intuitive, no-code controls to meet complex business requirements and deploy them natively to any data platform.
Empower Collaboration with Guardrails
Enable security and data teams to collaborate effectively—delivering faster, safer access to the data that powers analytics and AI while maintaining centralized visibility and consistent policy enforcement.
Enforce Access Policies as Data Moves into Power BI
When data moves from platforms like Snowflake or Databricks into Power BI, source-level security controls often break—exposing sensitive data and creating compliance risk. The alternative—coding SQL views for each access scenario—is time-consuming, developer-dependent, and difficult to maintain. TrustLogix removes this complexity by enforcing consistent, natively deployed access policies across Snowflake, Databricks, and Power BI, ensuring continuous protection from source to dashboard.

Simplify Access Control While Ensuring Global Compliance
Reduce complexity by replacing rigid, role-based access with fine-grained controls applied consistently across your environment. TrustAccess supports RBAC (Role-Based), ABAC (Attribute-Based), and ReBAC (Relationship-Based) access control models to ensure every user receives only the entitlements they need—at scale and with least privilege. A centralized control plane unifies policy management to address complex business requirements, including regional and jurisdictional compliance.
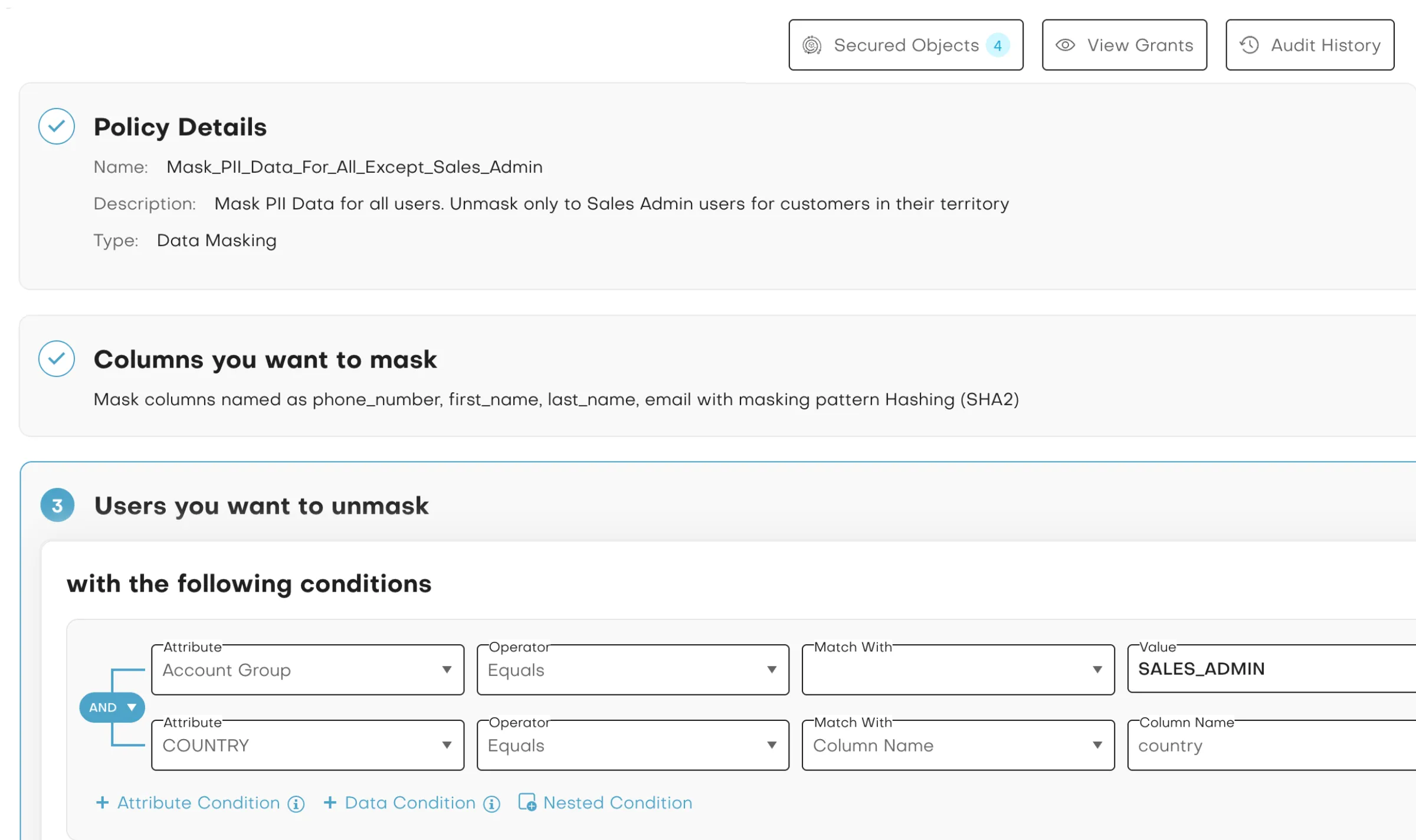
Provision Data Access at the Speed of Business
TrustLogix enables faster, more secure data access by combining self-service provisioning with federated governance. Data owners can organize domains, define policies, and collaborate across teams without waiting on IT, while centralized oversight ensures consistency and compliance. Native integrations with platforms like Snowflake and automated workflows streamline approvals and policy enforcement, so users get the access they need quickly—without broad permissions or developer bottlenecks.
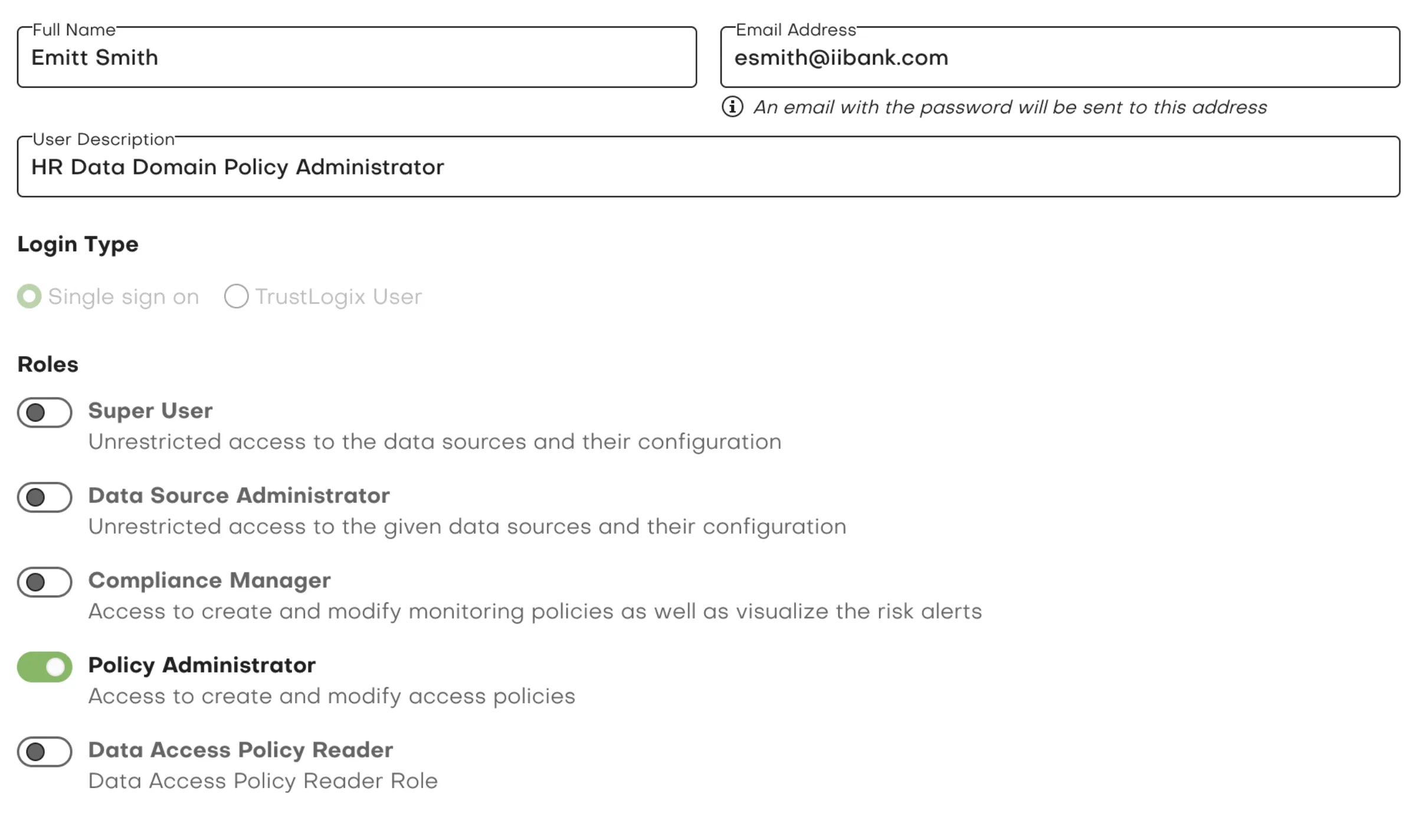
TrustLogix runs on top of Snowflake out-of-band, consuming only metadata without accessing the data. It deploys policies across multiple Snowflake accounts, ensuring uniform policy enforcement. With a single-pane-of-glass, policies are applied automatically, providing real-time protection without the need for manual deployment.


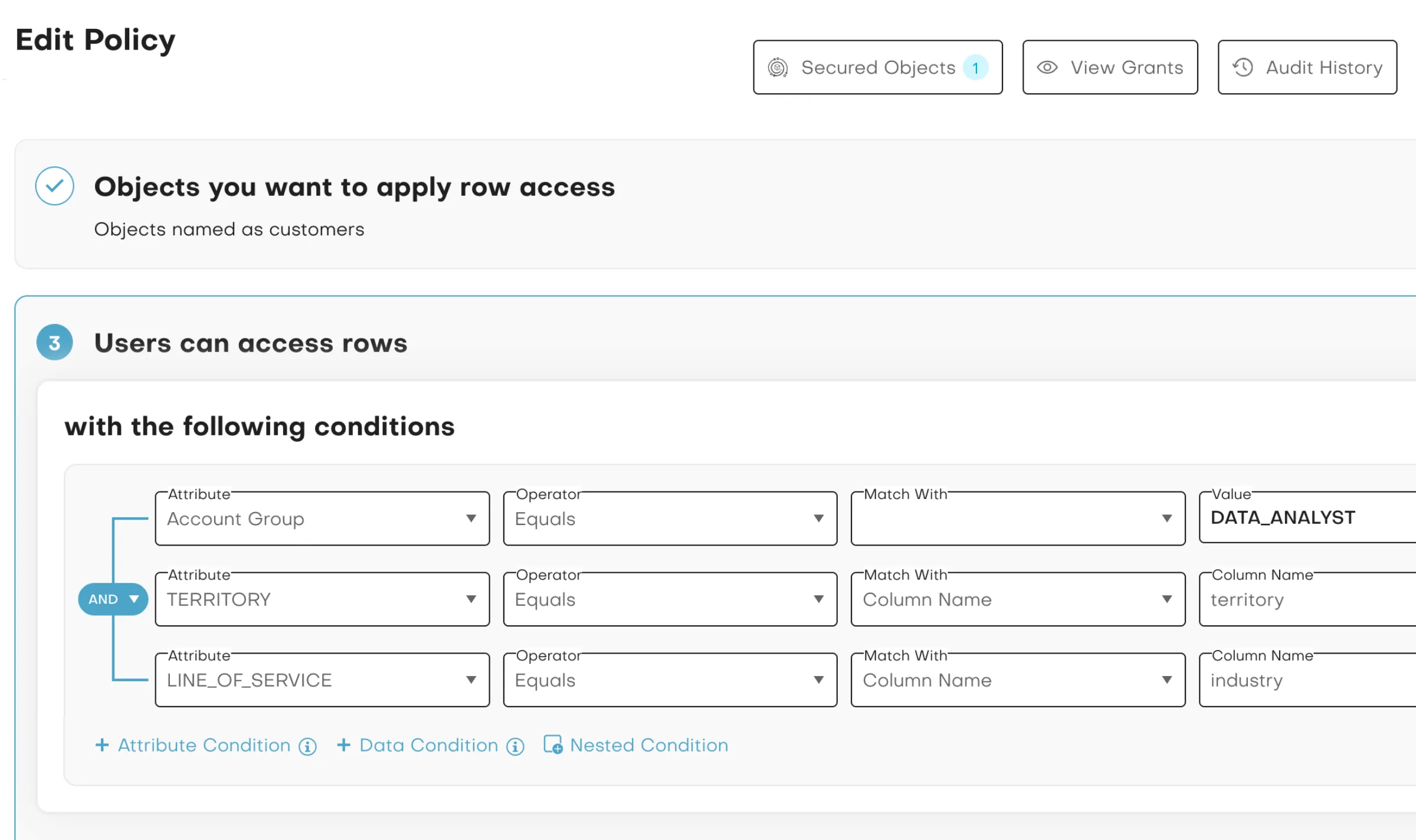
Streamline Policy Creation for Faster, More Secure Access
Simplify and accelerate access policy implementation with a no-code approach that eliminates complexity and developer dependency. Define policies once and deploy them consistently across any data source. Create masking rules, row-level access, and object-level controls tailored to business needs. The platform automatically generates the underlying SQL, so no custom coding or developer effort is required.
TrustAccess FAQs
Discover the answers to your most pressing questions about the TrustLogix platform.
TrustLogix ensures consistent least-privilege policies across Snowflake, Databricks, Power BI, and beyond by extending source-level controls everywhere your data lives. With the TrustAccess policy framework, RBAC and ABAC rules are defined once and applied consistently across cloud, on-premises, and AI platforms. Masking rules, row-level filters, and entitlement restrictions follow users automatically so they only see what they’re authorized to access. Continuous monitoring detects policy drift, misconfigurations, or overly broad permissions before they create exposure. The result is simplified governance, reduced compliance risk, and faster, more trusted access to data and AI.
Experience TrustLogix in Action
Schedule a call to discover how TrustLogix can accelerate your AI initiatives with faster, safer data access.










