Unify Data Visibility and Control for Secure Business Outcomes
Uncover access risks in minutes and gain continuous visibility across your data landscape—ensuring focused protection for the information that drives your business. TrustDSPM unifies visibility and control to show which data is most critical, who’s accessing it, and where exposure exists—using AI-powered intelligence to enable proactive risk remediation and guide policy refinement for least-privilege access. By extending unified visibility and control across hybrid, cloud, and on-prem environments, TrustLogix strengthens compliance, reduces exposure, and accelerates secure business outcomes.
See, Control, and Prove Data Security Everywhere
Accelerate Data Project Approvals with Real-Time Visibility of Data
Gain instant visibility into data sensitivity, usage, and movement to demonstrate proper access governance and reduce approval delays.
Eliminate Risky Access and Strengthen Policy Management
Identify ghost users, excess permissions, oversharing, and entitlement drift—then remediate issues and update policies with AI-powered recommendations.
Meet Compliance Requirements Without Manual Effort
Generate audit-ready views for SOX, GDPR, and HIPAA—accelerating compliance reporting and reducing custom coding.
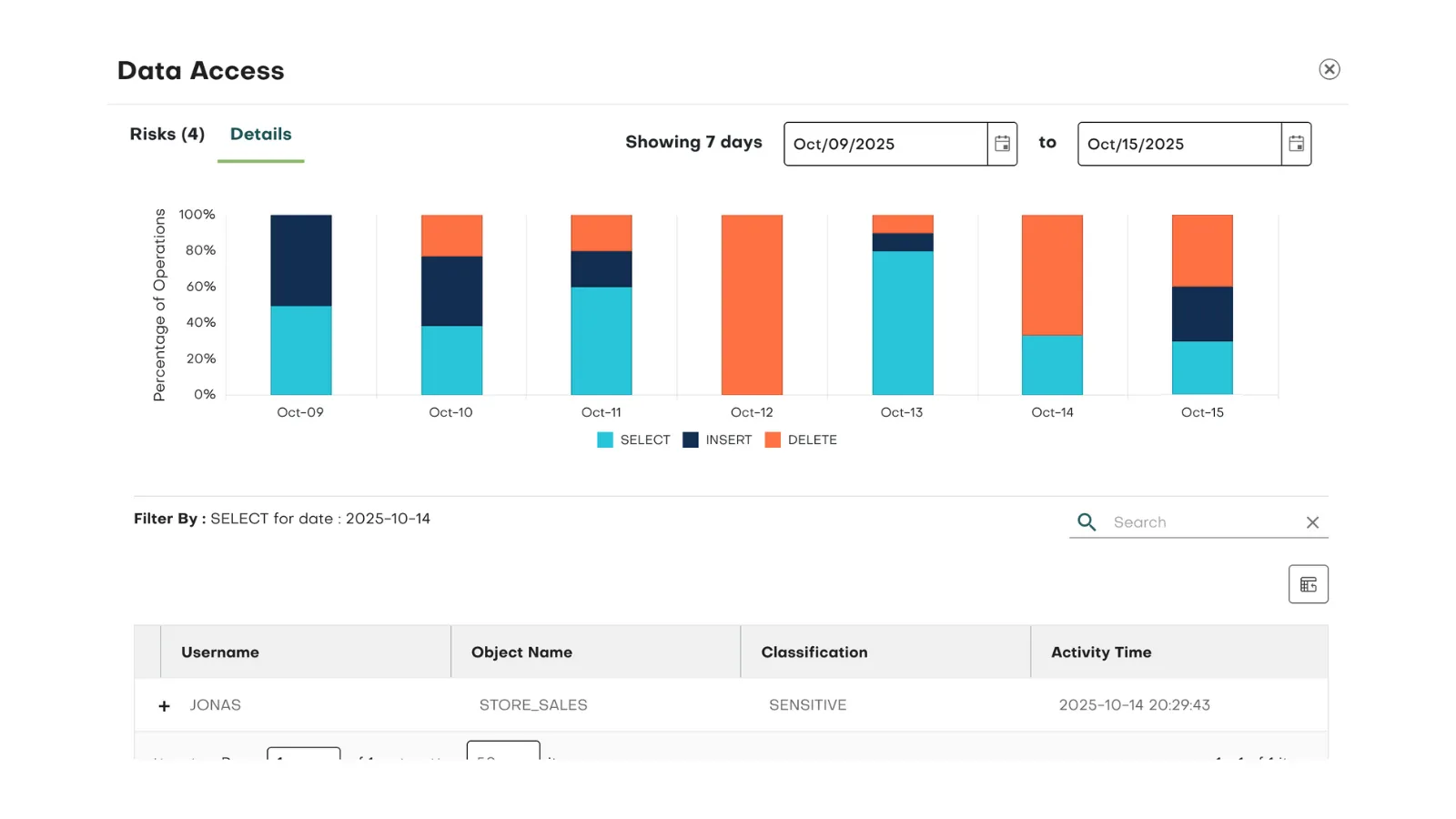
Protect Sensitive Data As It Moves Through Your Enterprise
Monitor and visualize data flows across your hybrid and multi-cloud environments to ensure sensitive information stays protected. Detect exfiltration risks, shadow IT applications, and cross-region sharing, while applying the right controls—such as masking policies, whitelisting, and access monitoring—to prevent unauthorized exposure and maintain compliance.
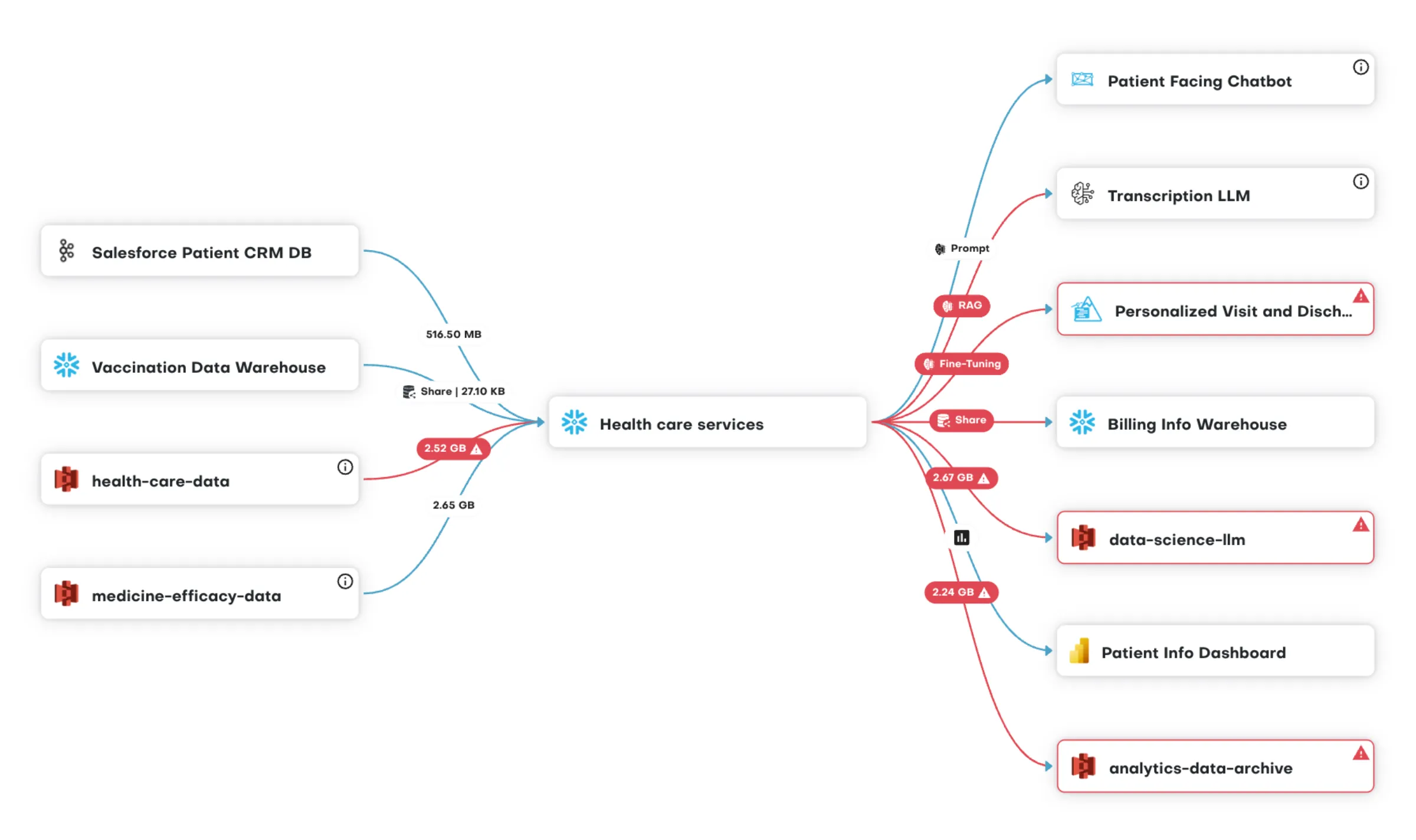
Simplify Role Management and Rationalize Permissions
Navigate role hierarchies at enterprise scale with a business-friendly console that visualizes inheritance and highlights which roles grant access to what data. Analyze user access patterns—including what data users can access and when they last used it—to uncover over-permissioned accounts, unused entitlements, and overlapping roles. Designed for large organizations with thousands of users and complex access requirements, TrustLogix makes it easy to prune unnecessary access, align users with functional roles, and eliminate spaghetti permissions—streamlining your path to least privilege.

Streamline Compliance and Reduce Audit Costs
Continuous monitoring and prioritized remediation ensure compliance with HIPAA, GDPR, PCI-DSS, and internal mandates. With prebuilt reports—covering entitlements, privilege analysis, and data classifications—you can respond to auditor requests quickly and accurately, without custom queries or manual effort.

Snowflake offered ease of use, enhanced performance, and key insights, while TrustLogix quickly integrated, providing Role and Attribute-based access and dynamic masking to help us build robust security in a highly regulated industry like ours.


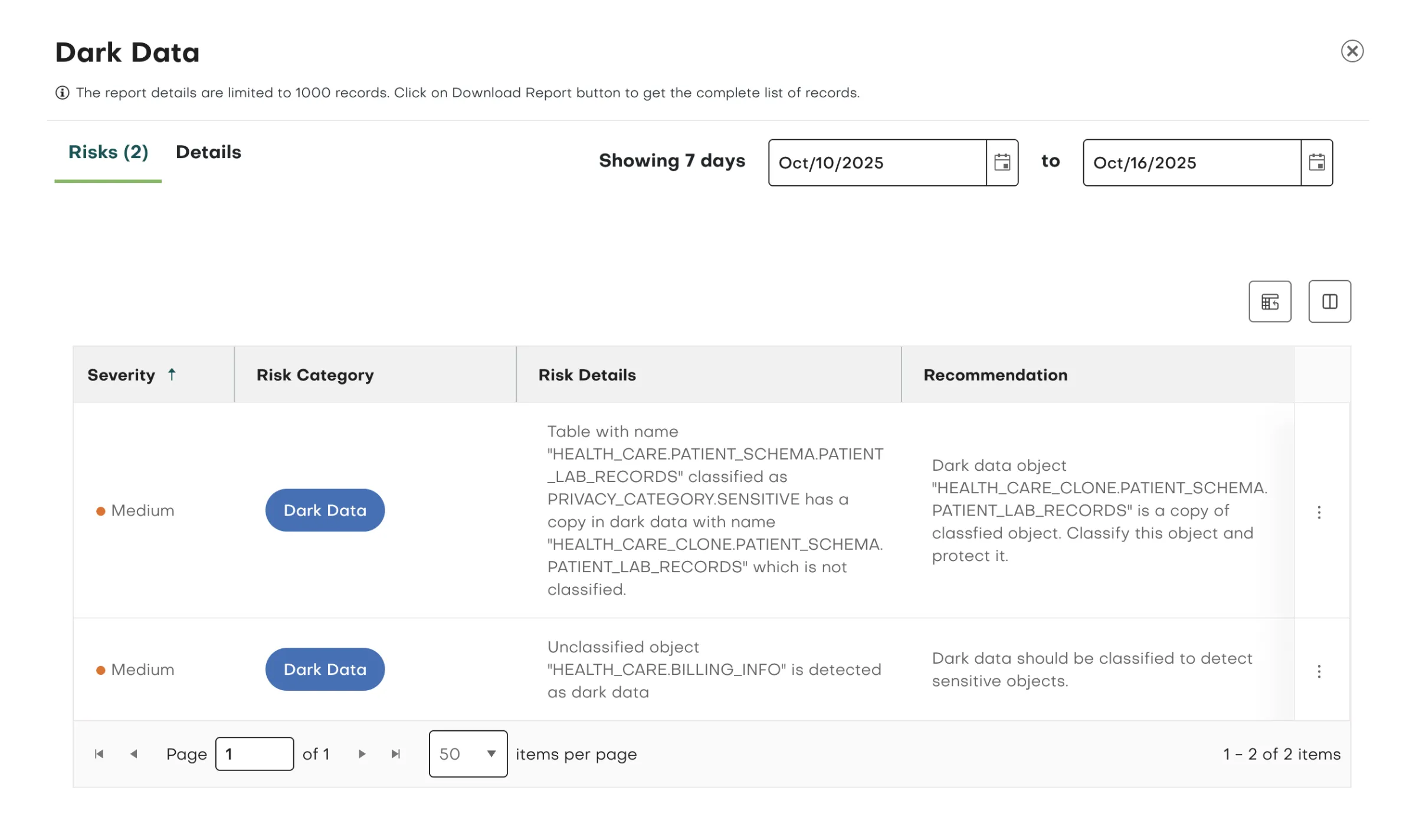
Reduce Data Attack Surface and Storage Costs
Uncover unaccessed and unclassified data so it can be archived or properly managed—reducing both risk and cost. By eliminating forgotten data that increases the chance of unauthorized access, preserving classification to prevent unprotected duplicates, and removing stale data that inflates storage costs without adding business value, you strengthen security while optimizing resources.
TrustDSPM FAQs
Discover the answers to your most pressing questions about the TrustLogix platform.
TrustLogix continuously monitors data movement across cloud and hybrid environments, giving security and data teams near real-time visibility into what tools are connecting, what data is being transferred, and the risks involved. Without ever touching the data itself, the platform flags unapproved transfers, risky cross-account or cross-region sharing, and exposure of PII or confidential data. This continuous oversight ensures sensitive information stays protected while enabling faster, more secure adoption of analytics, ML, and AI across clouds.
TrustLogix helps you streamline compliance and cut audit costs by generating audit-ready views for frameworks like SOX, GDPR, HIPAA, and CCPA—without custom coding or manual work. With integrated, no-code controls for masking, row filtering, and fine-grained access, enterprises can demonstrate a compliant data posture across diverse state and global regulations. The result is faster reporting, lower overhead, and continuous assurance for both internal stakeholders and external auditors.
Experience TrustLogix in Action
Schedule a call to discover how TrustLogix can accelerate your AI initiatives with faster, safer data access.